Mouse motion simulators may be a cyberthreat vector targeting remote workers and their employers, Kaspersky experts warn. The devices, which gained popularity with the advent of hybrid and remote work formats, could contain malware. Although these simulators may seem harmless and convenient at first, they may come from unknown sources and vendors and pose a serious threat to device security, potentially compromising the data of both the employee and the organization they work for.
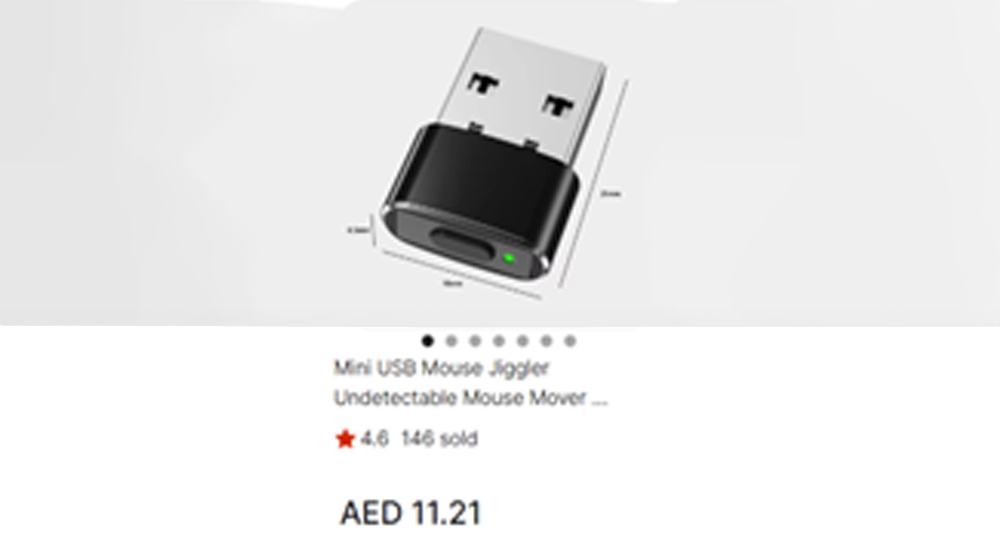
Also known as mouse jigglers, the devices are designed to create the impression that someone is working on the computer, preventing it from going into sleep mode and keeping the status indicators in corporate messengers online. These devices plug into the USB ports and simulate mouse movement on the screen. Throughout 2024, there were 3 billion local threats detected and blocked by Kaspersky’s main line of B2B and B2C solutions globally – these include malware that is spread via removable USB drives, CDs and DVDs, or that initially makes way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.). In the UAE, 19.2% of users faced local threats in July-September 2024.
“USB mouse simulators and similar devices could become an entry point for cybercriminals who can use them to gain access to confidential information or disrupt the operation of corporate digital systems,” warns Marc Rivero, Lead Security Researcher at Kaspersky. “Users should be mindful about connecting unknown USB devices to their corporate computers, and businesses should organize regular cybersecurity training courses for employees so that they are aware of potential threats. It’s also of vital importance to have reliable endpoint protection on corporate devices that can detect and neutralize suspicious activity. These measures will help protect the company from possible attacks and maintain data security.”