Mimecast made available the Decluttering Your Security Environment, the latest eBook from the Cyber Resilience Think Tank (CR Think Tank). The eBook is designed to provide expert insight and prescriptive advice to global industry influencers on how the industry may be to blame for all this complexity in security environments, best practices to effectively reduce security risk by minimizing complexity, and considerations for hiring the next generation of security professionals.
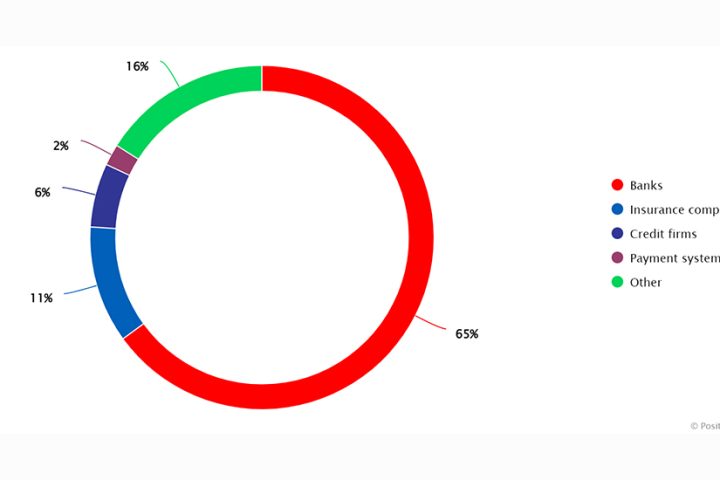
The explosion of cloud, mobile technology, social media and Internet of Things in the enterprise has led to a much larger attack surface for cybercriminals to exploit. To defend this larger attack surface, companies often acquire new technology. In fact, the average number of security tools in an enterprise is 75 according to some industry reports. Although well intentioned, this approach can be counterintuitive, as it results in too much complexity.
“Controls are a drag coefficient on people, data, and business processes,” said Malcolm Harkins, chief security and trust officer at Cymatic. “When you have too much friction in your environment because of the controls, you’re actually creating a systemic business risk for your organization.”
“[The skills gap] is something we have largely created for ourselves,” said Sam Curry, CSO at Cybereason. “It’s the complexity issue that has manifested itself in human form. It’s hard to find someone that knows 75 security solutions. You need to find a unicorn, and you never do. But if you didn’t have that complexity, you may not need a unicorn after all.”
CR Think Tank members gathered earlier this year to discuss how the complexity of a security environment can contribute to inefficiencies and ultimately, risk. Decluttering Your Security Environment details how security environments became cluttered in the first place, how it’s directly related to the cybersecurity skills gap and what organizations can do to minimize complexity. This report offers key insights to reduce the overall risk of an organization through simplifying IT infrastructures, helping to improve the effectiveness of their security environments. Specifically, the CR Think Tank members offer three key points for organizations preparing to declutter their IT security environment.
Know what you have, use it and connect it. As security vendors make advances to their products, companies may not be aware of new features and functionality. A key first step is to turn on all of the relevant features when assessing what products are needed.
Don’t bite off more than you can chew. Consider a plan where you take a methodical approach to see incremental improvement over a finite period. Even if the changes are minute, they can add up to a more secure, less complex environment over time.
Consider your resources. When adding new services to the security stack, ensure that it’s correct for the environment, specifically the resources and employees required to implement and manage it.
“Despite the number of tools and technologies on the market rapidly multiplying, the rate of attacks isn’t slowing down,” said Joshua Douglas, CR Think Tank member and VP of Threat Intelligence at Mimecast. “Organizations often struggle to navigate through the complexity of having multiple security tools and under-resourced IT and security teams. There’s a need for the industry to work better together to help improve organizations’ security postures.”