The drive towards digitalization has long been an ambition of organizations across the world. The transformational potential of digitalization is seemingly limitless.
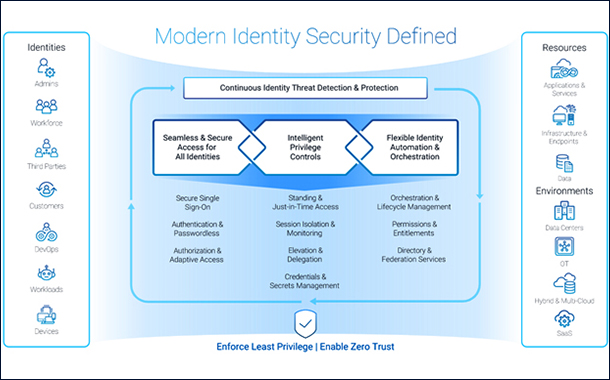
With the expansion of remote working models and ongoing migration to cloud-based services, the environment for attackers has become increasingly target-rich. As more and more devices are expected to be connected to remote networks, there’s a need to create new identities. However, each of these identities offers a potential weak point for bad actors to exploit the system.

With a rise in impersonation & spear-phishing attacks and targeted attacks to steal high-value identity credentials, it is essential for leaders to foster a change in their approach and culture. The importance of understanding the management of access and privilege rights must become second nature across teams and departments.
The protection of credential identities must be considered paramount in defending against malicious intent. Many organizations are still assigning and tracking identities manually. Passwords and keys remain unchanged for a longer period and even when employees or users no longer require access, they are retained needlessly. This practice increases identities to data breach or attack. Dormant accounts can be exploited and used as an entry point. If non-human credentials such as applications, DevOps Secrets, RPA bots etc., are not continually monitored and secured, they pose similar risks. Critical data and systems are only as safe as their weakest link. An accelerated transformation and digital business require a holistic, risk-based approach to secure human and non-human identities.
Building a Defense:
CyberArk solutions can help organizations by ensuring potential gaps in the security are closed. CyberArk can help to reduce the surface of attack by working to address risks in legacy IT services and infrastructure, managing credential security & supply chain risk, and ensuring successful adoption of cloud-based services, therefore, guaranteeing delivery of safe and effective processes.
CyberArk can help to reduce the surface of attack, ultimately ensuring safe and effective processes can be delivered:
- CyberArk’s DNA discovery and audit tool provides valuable insights into an organization’s exposure to risk, identify systemic weaknesses, help in quantifying the risk level & DNA highlight areas where a potential breach may occur and therefore, point towards ways to mitigate risks.
- Cloud identity entitlements and Privileges are managed and maintained across AWS, Google Cloud Platform, and Microsoft Azure. Risk reports using CyberArk AI discover, isolate, and record risky behavior for control, audit, and output in the entity’s Security Operations Centre (SOC).
- CyberArk’s Privileged Access Management (PAM) capability delivers secure management of Privilege throughout the entire life cycle of identity by reviewing and certifying access and ensuring segregation of duties. Sitting in front of either an existing legacy or modern Cloud architecture, CyberArk integrates “anything and everything”, creating an air gap between end user and asset.
How Does This Help?
- Infuse privilege controls to help isolate and stop attacks. Give humans and machines access to everything they need, at just the right time, while protecting critical assets.
- Manage the lifecycle of identities and take control of excessive permissions to enforce the least privilege.
- Secure all credentials and secrets used by non-human users. Eliminate hard-coded credentials in applications. Rotate credentials based on policies.
- Authenticate applications and containers using native application attributes and role-based access controls. Record key events with tamper-resistant audit.
- Zero Trust third-party privileged access: Provide external vendors with fast, easy, and end-to-end encrypted privileged access to critical internal systems.
Why CyberArk?
For more than two decades CyberArk has been in the vanguard of information security and identity management. Its Remediation and Red Team have been instrumental in helping organizations recover from some of the most serious security breaches during this century.
Widely recognized as the leader in Privileged Access Management, CyberArk solutions are used by nearly 7000 customers in 110 countries, including more than 50% of Fortune 500 companies and across a broad spectrum of both public and private sector organizations. CyberArk is the global leader in Identity Security. Centered on privileged access management, CyberArk provides the most comprehensive security offering for any identity — human or machine — across business applications, distributed workforces, hybrid cloud workloads, and throughout the DevOps lifecycle.














