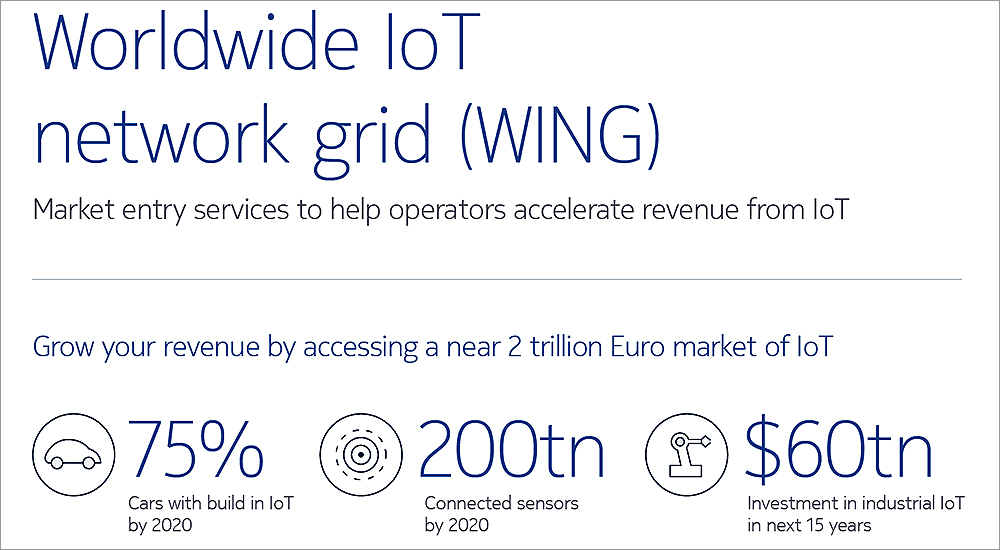
Nokia releases off the shelf, vertical market IoT solutions for global operators
Nokia launched off-the-shelf Internet of Things packages to help operators win new business in vertical IoT markets. In addition to enabling operators to achieve a fast time to market, the packages simplify










