It is predominantly observed that information security and project management are at loggerheads. Most commonly, projects have tight deadlines and somehow it is widely believed that information security slows down project delivery. So why should we not just ignore the information security requirement and focus on meeting deadlines?
Let me run you through a few scenarios to understand the importance of information security, especially in an IT project.
- You, the project manager, are informed that one of your resources shared the source code of a critical application with a competitor of your client.
- Just after the go-live, the webserver was brought down by adversaries who executed a successful SQL injection attack.
- A day before going live, your project folders on a shared location are inaccessible due to ransomware, which was sent to the project coordinator in her email earlier that day.
Each scenario demonstrates lack of information security control in each of the information security triad.
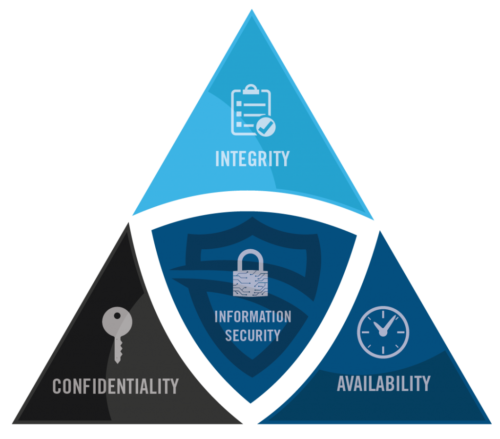
To avoid or minimise the impact of such a catastrophe, information security should be taken into consideration from the very beginning of the project management lifecycle. Considerable attention should be paid to incorporate information security best practices into each phase of the project management lifecycle.
Project managers are not expected to be security experts, but having information security in each phase of a project will enable the project team to deliver a more secure system, process, and infrastructure.
So what does typical project management look like and how does it facilitates an IT project and its executions? Here we take waterfall methodology as an example:
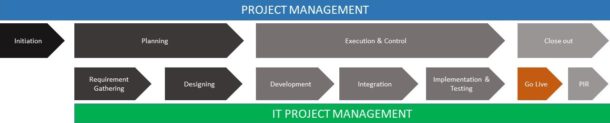 Prior to initiating any project, a business case is developed including high-level project objectives and requirements along with a cost-benefit analysis and the project feasibility. This phase is usually called the pre-project phase but it is not the focus of our discussion here.
Prior to initiating any project, a business case is developed including high-level project objectives and requirements along with a cost-benefit analysis and the project feasibility. This phase is usually called the pre-project phase but it is not the focus of our discussion here.
Initiation
The initiation phase is the most preliminary phase in any project management lifecycle. It usually begins with a project charter defining project scope, project timelines, identifying stakeholders, etc. Once the project is greenlit and project initiation document or a project charter is approved, the project managers should engage the security team to ensure the following:
- Information security objectives are incorporated into the project objectives. For example, the delivery of a secured system could be listed as one of the objectives.
- High-level Information security requirements are defined.
- Risk assessment is performed and all project risks, including information security risks, and their implications are detailed in order to identify necessary controls.
Planning
The planning phase is the most important phase and the key to a successful project . This is where the project plan is developed. In this phase, the information security team, in coordination with the project team, should:
- List the authorised hardware, software and systems to be used during the project.
- Ensure that the segregation of duties are clearly defined to prevent conflict of interest and to detect control failure.
- Identify potential threats and assess security risks such as a malicious attack, whether internal or external, that may occur during the project or a key resource that may not be available during the project.
- Allocate a budget to reduce the negative impact of such uncertain events.
- Agree on the change management practice to avoid unexpected data loss or system failure due to unrecorded changes.
- Run backup and restore jobs regularly during the project to guard against data loss due to unexpected crashes or errors.
- Develop the communication plan specifying the method, frequency, audience, guidelines and technical standards for communication such as:
-
- A document must be encrypted before sharing it over the internet.
- Meeting minutes shall be limited to only authorised personnel via secure method SFTP, encrypted emails or password-protected files.
- List the authorised Instant messaging tools which should only be allowed to use during the project.
Execution and control
This phase is often considered as the meat of the project. Usually in IT projects, this is the development, integration and implementation phase of the system, software or infrastructure. The project team with the support of the security team should ensure that during the execution and control phase:
- The physical security of the systems and development environment is controlled and monitored.
- All IT assets used in developing the system are protected using various endpoint protection tools such as anti-malware, host-based intrusion prevention systems, sandboxing and host-based firewalls to protect the systems from internal and external threats.
- Access control is monitored and auditing is enabled all the time for all authentication and authorisation requests.
- The secure configuration is taken into consideration during hardware and software deployment.
- Traffic flow is controlled and secured between resources using various methods and technologies such as encryption, micro-segmentation, firewalls, etc.
- Application software security passes all the relevant security checks before it goes into production.
- An adequate backup strategy is followed to backup critical resources even during the implementation.
- Systems are tested against their expected functionality, performance, availability, backup/ recovery, maintenance, and security.
- Segregation of duties is practiced to avoid conflict of interest and control failures.
Closeout
Closeout is the last phase in the PMLC. In IT Project Management, it is the phase where the post-implementation review, PIR, exercise is conducted after the Go-Live to evaluate whether the objectives of the project were met and If security was included in the initiation phase with agreed information security deliverables. Project handover should be organised after verifying those deliverables.
In addition, any security experiences and lessons learned should be documented and residual risks should be noted in the risk register for further improvements in controls.
Lesson learned can also be one of the most effective ways to establish a security culture in your organisation over the long-term.
By Zahid Syed, IT Architect/ Security Officer at Abu Dhabi Ports.















