The surge in registration and observation of new domains related to the Russian invasion of Ukraine has been over for some time. Nevertheless, our research shows that low levels of new phishing campaigns, donation scams, and other suspicious activities are still being launched in attempts to take advantage of Ukraine’s crisis. This article describes trends in Ukraine-related domain activity from the start of this year until now. In particular, we can see how newly registered domains were leveraged for both malicious and legitimate purposes in response to the crisis.
Our threat intelligence group has been monitoring cyber activity related to Ukraine since the beginning of the invasion. Immediately after Russia entered Ukraine, we created analytics designed to identify suspicious domains related to the crisis. We previously published about the dramatic rise in scams, the distribution of Agent Tesla malware, and the spread of Remcos malware. These analytics allow us to process a very large amount of DNS activity daily and focus our attention on a manageable subset of new domains. We also wanted to ensure that the sudden rise of legitimate fund raising activities were not inadvertently blocked and we made our ongoing findings available via GitHub.
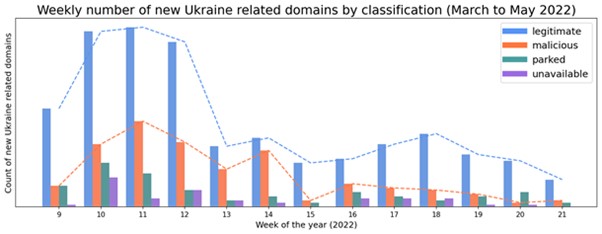
Since February, we investigated hundreds of indicators, of which we determined that 61% were legitimate sites, 23% were suspicious or malicious content, 11% were parked domains, and 5% were unavailable. We have added over a thousand domains to our GitHub repo. Figure 1 below displays a comparison between the legitimate, malicious domains (in this case, domains that were marked as suspicious, phishing, malware, or spam), parked and unavailable content.
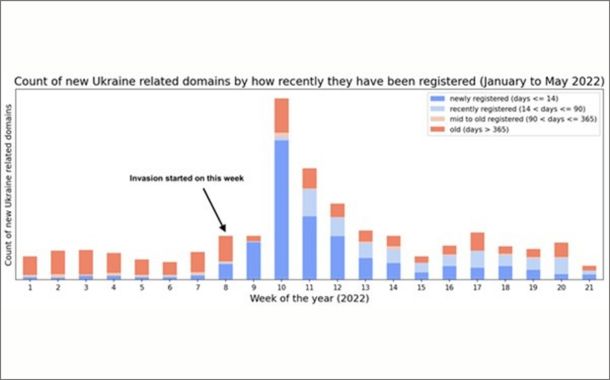
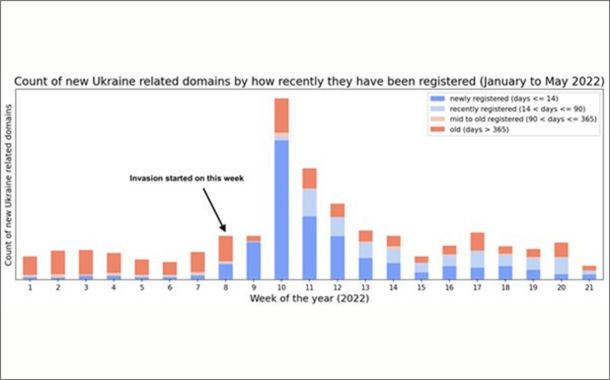
Overall, our data shows that the volume of legitimate domains is greater than malicious websites in our environment. The surge in newly observed domains began in the first week after the invasion, the beginning of March – week 9. For several weeks, many legitimate sites were created to help provide relief to the people of Ukraine; however, cyber threat actors and scammers also took advantage of the crisis, creating their own sites and adding to the volume of newly observed domains.
By the end of March week 13, the number of domains started to decrease, and the number of newly observed domains in our data began to stabilize, as depicted in Figure below. The most recent trends, beginning in April week 14, show that, on average, there continues to be a higher – though only slightly – number of newly observed domains legitimate and suspicious, in comparison to before the invasion.
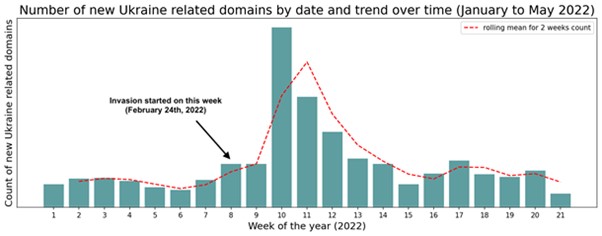
Figure below depicts the fluctuating trend of newly registered versus previously registered domains. In the early days of the conflict we detected a major increase of newly or recently registered domains. The most significant period was in week 10, in which the volume of both legitimate and malicious domains rose greatly. We determined that 61% of the newly registered domains that week were legitimate while 20% were malicious, the remainder belonged to the other categories listed at the beginning of this article.
The daily percentage of new malicious domains in comparison to the total of new Ukraine- related domains is volatile across our period of analysis. However, as shown in below, there are spikes on certain days, with the highest average ratio of malicious sites occurring toward the end of March-beginning of April. The daily median percentage of new malicious domains compared to the total is 34%, illustrated by the horizontal red line in the graph.
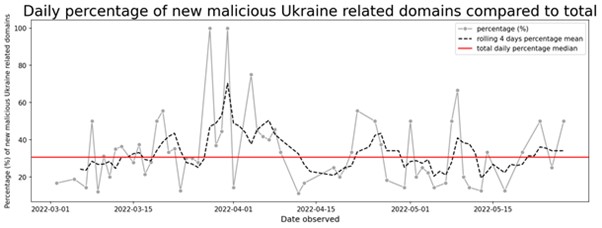
Although the number of malicious domains is trending down, users should remain vigilant. We know from previous experience that bad actors will continue to exploit individuals through email, malvertising, and other means as long as they can. For comparison, while covid related malware campaigns peaked in 2020, we still see them two years later. Users should carefully inspect requests for donations from organizations they are not familiar with and they should not click on links from unknown sources.