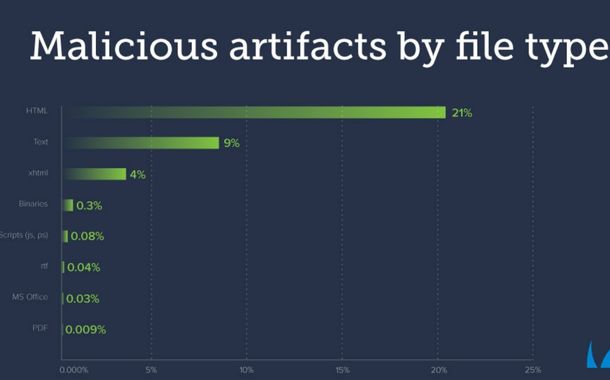
New research conducted by Barracuda Networks, has found that HTML attachments are by far the most used by cybercriminals for malicious purposes. The company’s analysis of millions of email attachments over the past month revealed that a whole 1 in 5 HTML attachments were malicious. By comparison, a meagre 0.03% and 0.009% of MS Office and PDF files respectively that were sent via the scanned emails were found to be malicious.
Explaining the growing popularity of HTML attachments as an attack vector, Toni El Inati – RVP Sales, META & CEE, Barracuda Networks said, “HTML attachments have become ubiquitous in email communications as they’re commonly used for system generated reports, updates, and notifications. They often include hyperlinks which users have become accustomed to clicking without first checking to see the full URL. It’s no surprise then that attackers have been quick to exploit this trust. Moreover, these attachments mean that attackers no longer need to place malicious links in body of the email and therefore allow them to bypass traditional anti-spam and anti-virus policies with ease.”
In analysing the modus operandi of the cybercriminals perpetrating these attacks, Barracuda’s experts found credential phishing and malware to be primarily motives. The research revealed that attackers commonly embed links to phishing or malicious websites within their HTML attachments. When opened, these HTML files use Java script to redirect users to third-party machines and request that they enter their credentials to access information, or download a file that may contain malware.
Barracuda’s researchers pointed out that these attacks are difficult to detect because the HTML attachments themselves are not malicious. Attackers do not include malware in the attachment itself but instead use multiple redirects with Java script libraries hosted elsewhere. Potential protection against these attacks must therefore consider the entire email along with its HTML attachments, looking at all redirects and analysing the content of the email for malicious intent.
The company’s cybersecurity experts also outlined key ways in which organisations can protect against the growing threat of malicious HTML attachments:
- Ensure the organisation’s email protection scans and blocks malicious HTML attachments. These can be hard to identify accurately, and detection tool often include a large number of false positives. The best solutions will include machine learning and static code analysis that evaluate the content of an email and not just an attachment.
- Train users to identify and report potentially malicious HTML attachments. Given the volume of these type of attacks, users should be wary of all HTML attachments, especially those coming from sources they haven’t seen before. Organisations should include examples of these attacks as part of their phishing simulation campaigns and train users to always double check before sharing their login credentials.
- If malicious emails get through, have post delivery remediation tools ready. These must allow the organisation to quickly identify and remove any instances of malicious email from all user inboxes. Automated incident response can help do this quickly before attacks spread through an organisation, and account takeover protection can monitor and alert security teams of suspicious account activity if login credentials were to be compromised.