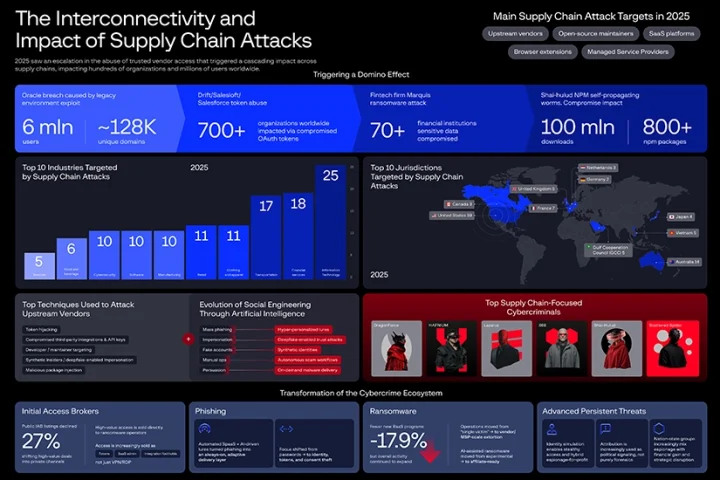
We sat down with Dmitry Volkov, CEO of Group-IB, at Black Hat in Riyadh, to discuss ways to combat cybercrime.
What are you spotlighting at Black Hat this year?
First of all, we aim to showcase almost everything we do, focusing on two main areas. The first is, of course, delivering innovative security services and products. We have a very diverse product portfolio that includes threat intelligence, managed cybersecurity services, EDR (Endpoint Detection and Response), XDR (Extended Detection and Response), network diagnostic analysis, brand protection, and more.
We are particularly well-known for our expertise in threat protection, especially in financial threats. This is why, when we observe significant fraudulent activity in the region, it becomes our responsibility to counter it. We know how to address these challenges, and we’ve been working successfully here in Saudi Arabia. This is what we are presenting at Black Hat.
The second area of focus is our services. We started our company as a cybersecurity services provider more than 20 years ago. From the very beginning, our mission was to be unique. Twenty years ago, we began as a digital forensics and incident response company. At that time, we realized we could add an extra layer to our offerings. While similar disciplines existed in countries like the United States, such as computer forensics and incident response services, we saw an opportunity to innovate further.
We understood that we could enhance our capabilities by conducting not only defensive operations but also investigations. This became our mission. Today, we provide digital forensics, incident response, and cybercrime investigation services, working extensively across Europe, the Middle East, and Africa.
What was your vision when you set up this company? How has it evolved over the years?
First of all, you need to understand that when we started, there were very few cybersecurity service companies. At that time, I was a student, as was my partner. We were just in the first year of our university studies. We were incredibly eager to gain knowledge—practical knowledge—about how cyber attackers managed to execute such amazing cyberattacks that bypassed all security controls. It became clear to us that this type of knowledge would never be taught at university.
So, what could we do? The idea was simple: let’s analyze real incidents. That’s how we started as a digital forensics and incident response community. Almost immediately, we realized that what we wanted to do was investigations. You need to understand the mindset of a student—there are no limitations, and your imagination is completely free. So, we decided, “Let’s do this.”
Later, we understood something else: no matter how big an organization is, how many security solutions they already have in place, or how mature their teams are, if we were being called to respond to incidents, it meant that something had already gone wrong. The attackers had bypassed all defenses. We saw gaps, and we started thinking about how we could help close those gaps because our clients were suffering from these vulnerabilities.
That’s how we began developing technologies. Initially, we created simple tools, such as solutions for collecting predictive threat intelligence, traffic analysis, and sandboxing. Over time, these technologies became more sophisticated, modular, and mature.
Our vision has always been to build a cybersecurity company that knows more than anyone else about incident response. We started as a company that was hungry for knowledge, and that hunger has defined us ever since.
Why is it so hard to mitigate ransomware attacks or DDoS attacks?
Mitigating DDoS attacks is not necessarily complex. If you have a robust telecommunications infrastructure in place—through your internet service provider rather than at the client level—it’s possible to protect against such attacks. This is especially true if the provider uses the right technologies. There are exceptions, such as when traffic is extremely dense, but these are rare. For an average dealership or mature organization, adequate protections should already be in place. You can simply subscribe to the appropriate service and forget about it.
Ransomware, on the other hand, is more complex. It operates like malware, and regardless of the specific type of ransomware, attacks are still possible. In large organizations, the sheer number of users and devices creates multiple vulnerabilities. Human error remains the weakest link. If even one device is compromised by malware, the attacker can perform lateral movements. This means they explore your network, gain more privileges, identify critical systems, and target them to cause maximum damage. In such cases, businesses are often pressured to pay a ransom to regain access to their systems.
What differentiates Group-IB in the cybersecurity market?
The cybersecurity market is highly challenging, but our differentiation lies in two key factors.
We don’t just focus on patching vulnerabilities. Many organizations take a reactive approach: addressing phishing with one solution, antivirus with another, and so on. However, this approach creates a false sense of security because it only addresses symptoms, not the root cause. Cyberattacks are carried out by real people. If an attacker successfully breaches your system once, they are likely to try again and again. Our approach targets the threat actors themselves, not just individual cyberattacks. This enables us to stop them at their source.
Another differentiator is our ability to hunt threats globally. Let me illustrate this with an example: Most cybersecurity vendors are highly centralized and based in regions like the United States or Israel. While these vendors are strong in cybersecurity, their focus is often limited to their local threats. Issues arising in other regions may receive less attention or be deprioritized. Our approach, however, is decentralized. We actively develop technologies that address threats globally, ensuring comprehensive protection regardless of location.
How do you approach threat hunting? Do you have a SOC in this region?
Yes, and this is another key differentiator for us. Let me share a story to provide some context. When we were based in a single country, we quickly realized the importance of developing localized threat intelligence. Many vendors in cybersecurity focus heavily on centralized regions like the United States or Israel. While they excel in addressing threats in those regions, they often overlook threats in other parts of the world.
Our success comes from our ability to build solutions tailored to regional needs, ensuring that we can address threats wherever they occur. This localized expertise, combined with our decentralized approach, enables us to provide better protection for businesses globally.