As cyberattacks escalate, Infoblox and Forrester Consulting investigated how security and risk, S&R, teams are using their DNS investments. The 203 respondents to the Accelerate Threat Resolution with DNS study reveal they most often use DNS to detect and block threats early in the kill chain, identify compromised devices, and investigate and respond to malware.
The top findings underscore DNS is an effective but underutilised tool for threat hunting and resolution even as alert fatigue challenges security teams to scale:
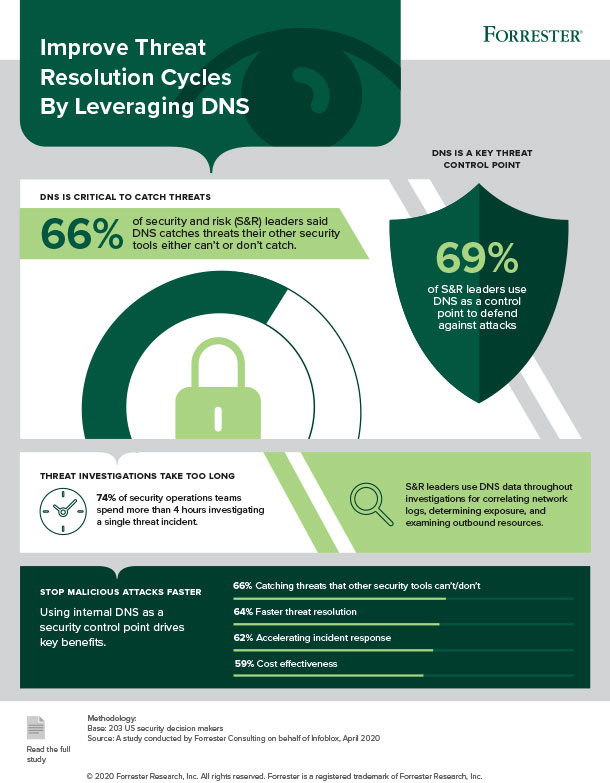
- 94% of S&R leaders either use or consider DNS as a starting point for threat investigations but only 43% of security and risk leaders rely on DNS as a data source to complete their investigations.
- 66% of respondents use DNS to catch threats, from DNS tunnelling or data exfiltration, domain generation algorithms, and lookalike domain attacks that other security tools miss but only 34% anticipate using internal DNS to stop malicious attacks at scale.
- 52% of leaders cite alert fatigue among teams and 51% report challenges dealing with threat triage; but only 58% of teams incorporate some automated processes for incident response.
Forrester surveyed 203 security and risk leaders from companies that earned more than $1 billion in annual revenue in the financial services, health care, education, retail, and government sectors for this report. Respondents include all levels of decision-making, including C-level, 48%, VP, 11%, Director, 34%, and Manager, 7%, roles across companies.
“It’s good to see the vast majority of security and risk teams recognise DNS as a powerful threat hunting tool,” said Anthony James, Vice President of Product Marketing at Infoblox. “At the same time, most companies are leaving money on the table by under-using their DNS investments. With 56% of leaders looking to improve security ROI, DNS can help save the day by providing a single pane of visibility into threats across the network and the edges.”
“DNS can also help automate some of the more repetitive tasks in threat hunting, freeing up security teams who spend an average of 4 hours per incident investigation to address more complex problems,” continued James. “DNS is one of the most cost-effective ways that companies can fortify their security and risk frameworks and maximise their existing security investments.”