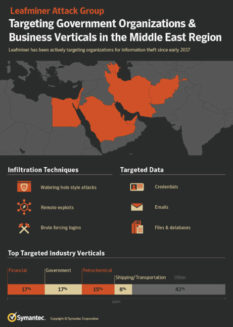
Symantec has uncovered the operations of a threat actor named Leafminer that is targeting a broad list of government organizations and business verticals in various regions in the Middle East since at least early 2017. The group tends to adapt publicly available techniques and tools for their attacks and experiments with published proof-of-concept exploits. Leafminer attempts to infiltrate target networks through various means of intrusion: watering hole websites, vulnerability scans of network services on the internet, and brute-force/dictionary login attempts. The actor’s post-compromise toolkit suggests that the group is looking for email data, files, and database servers on compromised target systems.
Leafminer’s arsenal
The download URL for a malware payload used in one of the attacks lead to the identification of a compromised web server on the domain e-qht.az that had been used to distribute Leafminer’s arsenal of malware, payloads, and tools within the group and make them available for download from victim machines.
As of early June 2018, the server hosted 112 files in a subdirectory that could be accessed through a public web shell planted by the attackers. In addition to malware and tools, the served files also included uploads of log files seemingly originating from vulnerability scans and post-compromise tools.
Targets
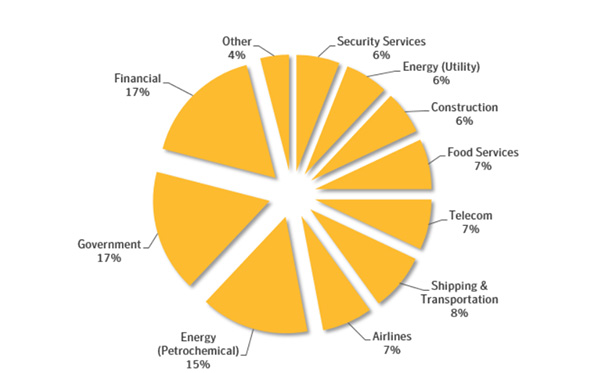
During the investigation of the Leafminer group, we were able to assemble a targeting profile from different sources including telemetry and log files hosted publicly on the attacker’s arsenal server.
Symantec detection telemetry shows malware and custom tools used by Leafminer on 44 systems across four regions in the Middle East.
Intrusion
Watering hole SMB credential theft
Our investigation of Leafminer started with the discovery of JavaScript code on several compromised websites in the Middle East. The obfuscated code was planted by the attackers to steal SMB credential hashes that could subsequently be brute-forced offline.
When executing the code, the browser creates an invisible image tag and sets the URL to an attack server using the file:// protocol scheme. On Windows machines this triggers a request to a remote server via the Samba networking protocol (SMB) that also transmits the user’s login NTLM hash. These hashes can be cracked to retrieve the original login password by methods of brute-force, dictionary, or rainbow table lookups.
Vulnerability scans and exploitation
The compromised web server used to store Leafminer’s arsenal hosted several public proof-of-concept exploits and exploitation tools.
This included the Fuzzbunch framework that was part of an infamous leak of exploits and tools by the Shadow Brokers in April 2017. Leafminer has developed exploit payloads for this framework (Table 2) that deliver custom malware through attacks against SMB vulnerabilities described by Microsoft. The EternalBlue exploit from the framework received worldwide attention after being used in the ransomware campaigns WannaCry in May and Petya/NotPetya in June 2017. The Leafminer operators use EternalBlue to attempt lateral movement within target networks from compromised staging servers.
Dictionary attacks
Another intrusion approach used by Leafminer seems a lot less sophisticated than the previously described methods but can be just as effective: using specific hacktools to guess the login passwords for services exposed by a targeted system. This type of attack was observed both via dedicated servers set up by Leafminer as well as staging servers compromised by the group.
Commands found in a readme text that was stored in a ZIP archive together with the hacktool THC Hydra in Leafminer’s tool arsenal represent online dictionary attacks on Microsoft Exchange and Remote Desktop Protocol services of regional government servers in Saudi Arabia. “Online” in this case refers to the attacker using the protocol of the targeted network service to quickly run through many password guesses.
Custom malware
Symantec identified two strains of custom malware used by the Leafminer group: Trojan.Imecab and Backdoor.Sorgu. Directly connected to this malware are several sets of reflective loader DLLs used as droppers or to execute specific commands on a compromised system.
The development of custom malware by Leafminer as well as some of the tools used for lateral movement show a preference for the .NET framework. We also observed that the attackers would download and install the .NET framework on compromised machines, supposedly in the situation that an operator would have remote access to the system but required .NET to run Leafminer’s custom tools. To this end, the command and control (C&C) server operated by the group hosted the legitimate setup executable for Microsoft .NET Framework 2.0 SP2.
Lateral movement and exfiltration
The discovery of malware and hacktools hosted on e-qht.az allowed us to correlate detection telemetry of potential Leafminer intrusions with tools made available for download to the group’s operators. Understanding the purpose of the tools used by the attacker gives a unique insight into the tactics and procedures used by Leafminer after the initial compromise of a target network.
We discovered a number of servers compromised by Leafminer that were used as staging systems to gain a foothold in the targeted network and execute attacks on intranet resources.
OrangeTeghal and Process Doppelgänging
One of the custom tools used by the Leafminer group is a rebranded version of the widespread post-exploitation tool Mimikatz.
While the logo and commands are identical to the original hacktool, the name was changed to OrangeTeghal. To evade security software while deploying this tool on compromised systems, the attackers use a technique revealed at Black Hat EU ‘17 in the presentation Lost in Transaction: Process Doppelgänging.
Ambitions blunted by inexperience
Leafminer is a highly active group, responsible for targeting a range of organizations across the Middle East. The group appears to be based in Iran and seems to be eager to learn from and capitalize on tools and techniques used by more advanced threat actors.
Leafminer has also been tracking developments in the world of cyber security. After the Heartbleed bug was disclosed it began scanning for instances of the vulnerability.
Protection
Symantec has the following protections in place to protect customers against Leafminer attacks:
Threat intelligence
Customers of the DeepSight Intelligence Managed Adversary and Threat Intelligence (MATI) service have received intelligence that details the characteristics of the Leafminer cyber espionage group and methods of detecting and thwarting activities of this adversary.
Best Practices
- Important passwords, such as those with high privileges, should be at least 8-10 characters long (and preferably longer) and include a mixture of letters and numbers.
- Emphasize multiple, overlapping, and mutually supportive defensive systems to guard against single point failures in any specific technology or protection method.
- Implement and enforce a security policy whereby any sensitive data is encrypted at rest and in transit.
- Implement SMB egress traffic filtering on perimeter devices to prevent SMB traffic leaving your network onto the internet.
- Educate employees on the dangers posed by spear-phishing emails, including exercising caution around emails from unfamiliar sources and opening attachments that haven’t been solicited.
- Understanding the tools, techniques, and procedures (TTP) of adversaries through services like DeepSight Adversary Intelligence fuels effective defense from advanced adversaries like Leafminer.


















