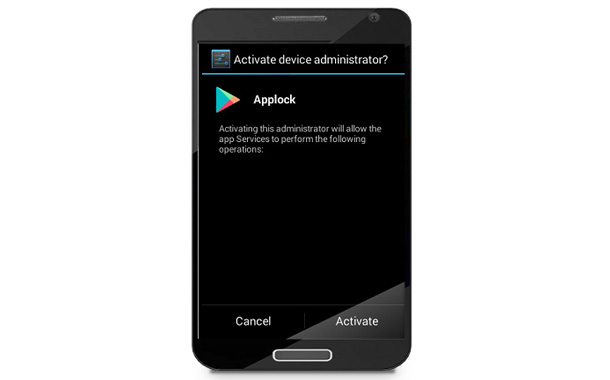
Using the Google Play icon while asking for admin privileges
Seven apps have been discovered reappearing on the Play store under a different name and publisher even after these have been reported. A set of apps has managed to reappear in the Play store even after having alerted Google and the original app was removed. The same code was published on Google Play with a slightly different name under a new publisher.
This malware (Android.Reputation.1) appears on the Play Store hidden in at least seven apps in the U.S. offering fun, useful, and sometimes insidious features. These include emoji keyboard additions, space cleaners, calculators, app lockers, and call recorders. None of the samples actually functions as advertised on Google Play pages. Once the app is installed, it takes various measures to stay on the device, disappear, and erase its tracks.
All of these apps have the same set of tricks designed to take advantage of the device user.
The malware is configured to wait for four hours before launching its malicious activity, so as not to arouse user suspicion straight away. The app is looking to raise the barrier for its uninstallation, and is usurping trusted branding to pull it off. The app uses the Google Play icon awhen requesting device administrator privileges. The app has the ability to change its launcher icon and its “running apps” icon in the system settings once installed. Again, it uses well-known and trusted icons—specifically that of Google Play and Google Maps—to allay suspicion.This configuration takes advantage of the legitimate and ubiquitous “Firebase Messaging” service, copying yet another service into a command and control (C&C) service.