SolarWinds is a provider of IT infrastructure management software. The company, headquartered in Austin, Texas, was founded in 1999 and is trusted by more than 320,000 customers in over 190 countries, including 499 of the Fortune 500 companies. In addition, the MSP business unit of SolarWinds, soon to be launched as a separate publicly traded company, N-able, serves more than 450,000 organisations worldwide.
Independent market analyst firm IDC has recognised SolarWinds as a leader in network management software, and Gartner ranks SolarWinds as third in the systems management market.
SolarWinds products focus on the individuals working in various IT roles: IT professionals. A career in IT can be exciting and rewarding, and most professionals with a passion for technology enjoy the responsibility to drive innovation for their employers.
But the job can be hard, too, as technology changes at the same pace as the demands of the business. To achieve and retain a competitive advantage, professionals need to be on top of challenges, both technological and financial.
The SolarWinds product portfolio spans more than 50 products to help organisations monitor and manage their IT infrastructure.
Meanwhile, most businesses face shrinking budgets because of the pandemic, but even before 2020, many companies were already under pressure from disruptive market changes, new competitors, and other factors. And shrinking budgets always include budget cuts for the IT department.
The usual result is an increase in workload with the same or even lower headcount. Therefore, teams need to rely on tools to solve problems now and tomorrow.
The SolarWinds product portfolio spans more than 50 products to help organisations of all types, sizes, and industries to monitor and manage their IT infrastructure, whether on-premises, in the cloud, or hybrid, or even multi-cloud.
The Orion Platform
The Orion Platform is the foundation upon which up to 14 different management tools operate. These tools work autonomously but are even more powerful when combined with others in the modular platform, and grow with the demands of the business, making it a strong system that can keep up with change.
Among those tools are popular solutions like Network Performance Monitor, NPM and Server and Application Monitor, SAM and other solutions addressing more specific problems with storage arrays or the performance of web applications or databases.
The Orion Platform is the foundation upon which up to 14 different management tools operate.
NPM is seen as the de-facto standard in network monitoring by market analysts and collects health and performance data from all elements in the network. It uses advanced features, like automated network diagrams and in-depth insights into complex devices, like load balancers or firewall clusters using an out-of-the-box API.
One of its highlights is a unique feature called NetPath, which visualises the path of applications from point A to point B.
NetPath shows problems with application delivery based on problems with the network on-premises, or at the ISP, or at the destination, which could be a public or private SaaS solution. Combined with other Orion Platform modules, the NetPath feature uses real-time information from various flow protocols and even detects changes in network device configurations as a possible root cause.
Other features, like the PerfStack dashboard, are rooted in the multi-module approach of the platform and allow you to compare different types of data, independent of its source or location. Most administrators use it to gain insights from correlated data to get the full picture within a few seconds, and even travel back in time to understand previous incidents.
These features and the ease of use have made the Orion Platform a popular product, which unfortunately has attracted advanced threat actors.
The cyberattack
On December 12, 2020, SolarWinds was notified of a cyberattack, later named SUNBURST. Authorities, customers, and shareholders were notified on December 14, and SolarWinds engineering teams had an emergency hotfix ready the following day. The SUNBURST attack was one of the most sophisticated and complex cyberoperations in history.
Security analysts rank the SUNBURST supply chain attack as one of the most sophisticated cyberattacks in history.
While investigations are still ongoing by governments, intelligence, and law enforcement agencies around the globe, and by private sector industry experts, SUNBURST was revealed to be a supply chain attack. SolarWinds was not the only target, but merely a method to get into other environments of interest to the attackers.
While SUNBURST in general was tailored to attack the Orion Platform environment, those sub-elements were tailored for specific customer environments. Security fixes for all affected versions have been available since December 2020.
US government and private-sector experts have stated their belief that a foreign nation-state conducted this intrusive operation.
During the investigations, another, unrelated vulnerability was discovered, called SUPERNOVA. SUPERNOVA is not malicious code embedded like SUNBURST; instead it is a malware that used a previously undiscovered API vulnerability of the platform.
In some environments, the perpetrators could bypass perimeter security and gained unauthorised access to the Orion Platform. They deployed an unsigned file specifically written to attack the system, and further deployed and utilised malicious code in a second step. This vulnerability has also been resolved in available updates.
The US government and private-sector experts have stated their belief that a foreign nation-state conducted this intrusive operation as part of a widespread attack on primarily American cyber infrastructure. To date, our investigations have not independently verified the identity of the perpetrators.
Lessons learned
Kevin Mandia, the CEO of FireEye, summarised these most recent events. “We have a need for shields up.” Leading security analysts rank the SUNBURST supply chain attack as one of the most sophisticated cyberattacks in history. Researchers at Microsoft estimated that based on the scope of the attack, around 1,000 engineers could have been involved full-time working on the operation.
Furthermore, threat actors have obviously become increasingly sophisticated, resourced, and well-funded. If backed by a nation-state, a hacker’s job is even easier, as a successful operation comes with great rewards, and in case of a detection, a government may shield the threat actor, which means a lower risk in general.
The attack makes clear that current software development procedures, many considered as best practices, are no longer safe.
Because of the complexity behind the attack and common practices in software development, the same strategy and tools have likely been used to attack other vendors as well. That is one of the reasons SolarWinds is communicating the issue and findings openly and sharing them with the greater IT community—and are working with other vendors. SolarWinds believes transparency is key in such a situation.
SolarWinds could reconstruct the events as logs were still available dating all back to 2019.
Each organisation should ask themselves “Who is in our supply chain?” and discuss possible risks with their vendors, contractors, and service providers. What we have dealt with was an attack on trust, or the trust chain, and gives even more reason to have a zero-trust environment: assume you are already compromised.
SolarWinds also learned the attackers planned and ran the operation over a long timeframe, and fortunately, SolarWinds could reconstruct the events as logs were still available dating all back to 2019. This taught us that keeping logs for 90 days, which is the default for many devices, software, and infrastructure, is insufficient and should be reevaluated.
Because of the complexity behind the attack the same strategy may have been used to attack other vendors as well.
The attack was a wake-up call for the industry and makes clear that current software development procedures, many considered as best practices, are no longer safe.
Secure by Design
With all the knowledge gained from investigating the attack, and help from leading cybersecurity experts, SolarWinds seeks to evolve into a company that is secure by design. These transformative efforts will require tremendous focus on security programs, policies, teams, and culture.
Some immediate steps were taken to further secure the internal environment, like deploying an additional, robust threat protection and threat-hunting software on all the network endpoints, including a critical focus on the development environments.
In addition, a password reset was enforced on all users in corporate and development domains. The credentials for all privileged accounts and all accounts used in building the Orion Platform and related products were reset. Remote and cloud access have been consolidated and accessing any internal SolarWinds resource requires multi-factor authentication.
Steps to enhance the product development environment include ongoing forensic analysis of the environment to identify root causes of the breach and remediation steps. More important is the move to an entirely new build environment with stricter access controls and deploying mechanics to allow for reproducible builds from multiple independent pipelines.
Keeping logs for 90 days, which is the default for many devices, is insufficient and should be reevaluated.
As improving the security and integrity of the software SolarWinds delivers to customers is the objective, the vendor is including additional automated and manual checks to ensure the compiled releases match the source code.
In addition, SolarWinds is expanding the vulnerability management programme to reduce the average time-to-patch and improve the way SolarWinds works with the external security community. Additional third-party tools expand the security analysis of the source code. Extensive penetration testing of the Orion Platform software and related products help identify any potential issues, which will be resolved with urgency.
One of the most visible steps already taken is the re-signing of all Orion Platform software and related products, and many other SolarWinds products, with new digital certificates. These digital code-signing certificates verify the authenticity of both the publisher and the code. Vendors apply for a certificate and certain certificate authorities will hand out a private and a public key. The public key is embedded into the code before publishing.
Modern operating systems check the integrity of a digital certificate upon installing software, and warn if the certificate is invalid, no longer valid, or not available at all. Most endpoint security solutions continuously check for certificate validation and, depending on the setting, could block the execution of files with invalid or revoked certificates.
In the case of a compromised certificate, it is industry-standard best practice to re-sign the software. SolarWinds not only re-signed the products of the Orion Platform, but all of its products and tools which used the compromised certificate.
This allowed SolarWinds to revoke the compromised certificate, so customers can keep updated solutions running in their environments without further changes or performance issues.
SolarWinds has seen a massive spike in cloud adoption on an international scale..
To assist customers with the digital code-signing certificate update process and provide further assistance outside regular update cycles in general, SolarWinds opened the Orion Assistance Programme, OAP.
The OAP provides upgrade and hotfix assistance to Active Maintenance customers by leveraging professional consulting resources who are experienced with the Orion Platform and its products. These guidance and support services are provided at no additional charge to Active Maintenance customers who were or are running one of the Orion Platform versions affected by SUNBURST or SUPERNOVA.
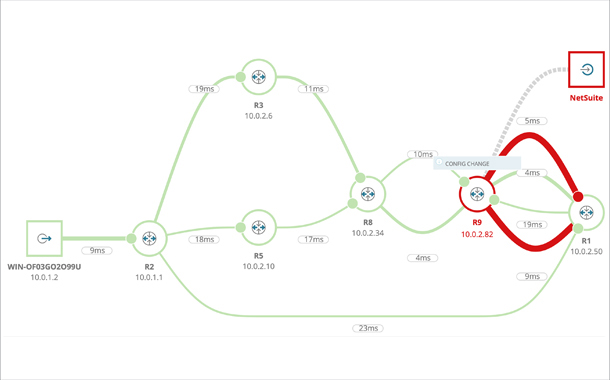
A typical engagement could last from a couple of hours for patching up to 24 hours to accommodate maintenance windows or support highly complex environments. The services are provided by members of the SolarWinds technical support team as well as its certified regional partners, including the Middle East region.
In summary, SolarWinds expects these efforts and plans to help it become a safer and more secure company.
Further innovations
While securing software is obviously the priority now, SolarWinds is also working on further innovations, products, and features. For example, SolarWinds is already using machine learning in some of its products and intends to enrich other products with this technology as well.
SolarWinds relies on its technology community of more than 150,000 registered members, THWACK, to keep a finger on the pulse of IT professionals. SolarWinds invites them to have a say in what features will be added to its products, which is a unique approach. For example, customers requested support for Google Cloud SQL managed databases, which SolarWinds is currently working on for its Database Performance Analyser.
Speaking of databases, SolarWinds learned database administrators are a group in need of more assistance, as many database administrators are put in the role because no one else would do it. Improving the support for those accidental database administrators is one of the missions for the future.
The reasons are simple: data sits at the heart of each organisation and is part of application delivery. Since the pandemic, SolarWinds has seen a massive spike in cloud adoption on an international scale, even in regions where public clouds were not popular before.
This means many organisations find themselves in uncharted waters and require assistance from local talents, service providers, and software vendors.
There is a good side to it, as many organisations have reflected on optimising their current IT procedures and policies. The idea is to work with what SolarWinds has and improve it.
Improving the support for those accidental database administrators is one of the missions for the future.
But more importantly, many corporations have accelerated their digital transformation strategies, and that is another trend in progress. And while this started in the private sector, where companies sought competitive advantages while facing adversity wrought by the pandemic, it moved on to the public sector as well.
The Middle East
SolarWinds has been active in the Middle East for many years now, and SolarWinds has built long term relationships with customers. One of the global, top ten SolarWinds deployments sits in the region.
SolarWinds has partnered with two distributors. Both distributors are SolarWinds Certified Professionals and provide on-site consultation and professional services.
The Middle East is a particularly interesting region. First, a lot of the technical infrastructure is new, compared to Europe or the US, which means there is less legacy tech to maintain. Also, the vendor landscape is more open, and SolarWinds see a good mix of different technology in many companies. The speed of change is also remarkable.
These are exciting times in an exciting region.
Transforming the security of organisations through programmes, policies, teams, and culture.

























