Lightly termed by a report as a ‘merry mayhem’, the Petya ransomware is predicted to hover around in the cyber crime world for long. Unlike WannaCry, the iteration of the codes are reported to be stronger, but is it ransom that the attacker is aiming for? Or is there more than the technical eye meets?
As the internet and the cyber world started bustling with the news of Petya (or NotPetya or GoldenEye as some reports state) since the wee hours of Tuesday, here is our opinion on the same with some deep insights from industry leaders.
The world once again woke up to a security reality check as Petya hit some major companies in Ukraine and Europe, slowly spreading to some parts of US and Asia that left the organizations to ponder over their security protocols once again. It was only a few weeks back when organizations around the world fought against the WannaCry attack. Where is the loophole now?
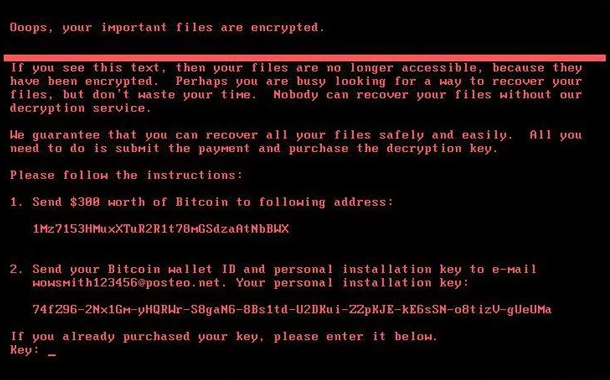
The latest ransomware, which is being dubbed as NotPetya, has surfaced as a serious mayhem that is not able to provide the decryption keys to the victims, even after they paid the ransom. Though experts are of the opinion that the NotPetya attackers have not repeated the mistakes that the WannaCry gang did, the situation has become very chaotic owing to the inability of the attackers in handling the payments.
The attack that is claimed to be seeded from a software update that was done in the Ukranian government systems, has encrypted the critical information existing in the systems, leaving the entire infrastructure crippled. According to Ukraine’s cyber-cops, as well as phishing emails booby-trapped with malware-laden attachments, financial software firm MeDoc was used to infect computers in the ex-Soviet nationOnce inside the network, the ransomware steals administrative credentials, giving it control over powerful system management tools like Windows PsExec and Windows Management Instrumentation.
 Taj El Khayat, Director for the Gulf, Levant & North Africa Region at F5 Networks, says “This latest wave of what looks to be ransomware is just another example of the real-world threats encountered by organisations, governments and countries all over the world. These attacks are upping the ante, as they hit services that affect people’s day-to-day activity; such as healthcare, postal services, and transport services. While the reported ransom demands of $300 to release the encrypted data seems low, this will scale up very quickly. The more concerning issue is how national infrastructure is being impacted. There is no easy solution to eradicate ransomware, but when the dust settles, the source of the compromises needs to be determined and remediated.
Taj El Khayat, Director for the Gulf, Levant & North Africa Region at F5 Networks, says “This latest wave of what looks to be ransomware is just another example of the real-world threats encountered by organisations, governments and countries all over the world. These attacks are upping the ante, as they hit services that affect people’s day-to-day activity; such as healthcare, postal services, and transport services. While the reported ransom demands of $300 to release the encrypted data seems low, this will scale up very quickly. The more concerning issue is how national infrastructure is being impacted. There is no easy solution to eradicate ransomware, but when the dust settles, the source of the compromises needs to be determined and remediated.
“Going into the new world of IoT and connected devices, with every element focusing on the application, the digital attack surface area will continue to grow. This gives the attackers more opportunities to infiltrate data. More focus needs to be put on the application and data security. In addition, more cyber security education should be integral in everybody’s daily lives.”
DON’T TAKE THIS TORTOISE LIGHTLY- ITS SLOW, BUT STEADY
 WannaCry had a far reaching effect within a few hours of its launch. In contradiction to that, Petya has so far affected 2,000 targets. Reports suggest that Petya or NotPetya has a more targeted approach to the infection. Security experts have warned not to take this as a setback in any way. Though the traits are similar to WannaCry, reports from across the world are saying that the victims have not received any decryption key against the $300 equivalent bitcoin that they paid. The email address to which the victims have to send the wallet id has also been reportedly shut.
WannaCry had a far reaching effect within a few hours of its launch. In contradiction to that, Petya has so far affected 2,000 targets. Reports suggest that Petya or NotPetya has a more targeted approach to the infection. Security experts have warned not to take this as a setback in any way. Though the traits are similar to WannaCry, reports from across the world are saying that the victims have not received any decryption key against the $300 equivalent bitcoin that they paid. The email address to which the victims have to send the wallet id has also been reportedly shut.
Steven Malone, director of security product management at Mimecast, says “Mimecast advises organizations never to succumb to the pressure to pay the ransom to regain access to their applications and data. There is no guarantee this will unlock files and further motivates and finances attackers to expand their ransomware campaigns.”
OOPS! THERE IS NO ‘KILL SWITCH’
Security experts had decoded a kill switch in the WannaCry attack that allowed them to control the spread of the same to some extent. No report of any such switch has surfaced so far, extending the horizons of vulnerability to greater extents.