NOTPETYA TRAITS
- Infects machines through the networks
- Extracts network administrator’s credentials
- Uses a modified version of EternalBlue
- Infects other systems using Windows PsExec and WMIC by using malicious codes
- The malware encrypts files on the host using 2048-bit RSA encryption
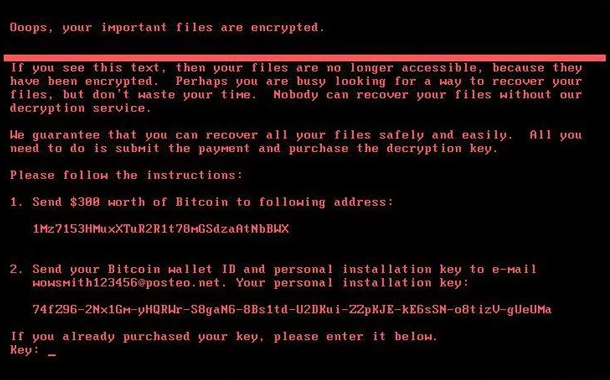
- Files are taken as hostage and locked
- A message pops up saying the files are encrypted and victims have to pay a ransom for the decryption key
PATCH OR LATCH…. WHERE IS THE CATCH?
 Since paying the ransom has not yielded any results so far, the question that arises is, what is the catch or where is the catch?
Since paying the ransom has not yielded any results so far, the question that arises is, what is the catch or where is the catch?
Was this attack launched just to get ransom or there is any hidden agenda behind this? Will patching the vulnerabilities work? Will latching other critical grids work?
To prepare for the next generation of ransomware attacks, it is imperative that organizations patch all systems aggressively against known vulnerabilities, establish a secure architecture that utilizes advanced cyber security defense technologies and execute a comprehensive data back-up plan for their organization,” says Steve Grobman, CTO, McAfee LLC.
 Nigel Tozer, Solutions Marketing Director, Commvault, says “The best option, to insure against data-mincing malware, is an in-house centrally managed backup solution. Whilst reverting to the backup prior to the infection might mean losing a limited amount of data, it is nominal compared to the impact of losing all your data permanently.”
Nigel Tozer, Solutions Marketing Director, Commvault, says “The best option, to insure against data-mincing malware, is an in-house centrally managed backup solution. Whilst reverting to the backup prior to the infection might mean losing a limited amount of data, it is nominal compared to the impact of losing all your data permanently.”
BE SAFE
“Cisco Talos analysis points out that, once this ransomware enters your system, it uses three ways to spread automatically around a network, one of which is the known Eternal Blue vulnerability, similar to how last month’s WannaCry attack unfolded. What’s clear from this, and recent attacks, is that organisations must prioritise patching systems to lower their risk profile. We have to patch as quickly as we can. In addition, making back-ups of key data is a fundamental of any security program
 Harish Chib, Vice President Middle East & Africa suggests the following measures to stay safe:
Harish Chib, Vice President Middle East & Africa suggests the following measures to stay safe:
- Ensure systems have the latest patches, including the one in Microsoft MS17-010bulletin
- Consider blocking the Microsoft PsExec tool from running on users’ computers. You can block it using a product such as Sophos Endpoint Protection. A version of this tool is used as part of another technique used by the Petya variant to spread automatically
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands
- Avoid opening attachments in emails from recipients you don’t know, even if you work in HR or accounts and you use attachments a lot in your job
 Lee Fisher, EMEA Security Specialist at Juniper Networks, says “Juniper Networks is aware of a new variant of the Petya malware family. The malware combines a number of existing techniques to spread across vulnerable clients. We have begun the process of analyzing today’s samples of Petya in the lab and can report that we are able to detect and prevent infection using our SkyATP and IDP technologies. Juniper will continue to update this blog as additional information becomes available.”
Lee Fisher, EMEA Security Specialist at Juniper Networks, says “Juniper Networks is aware of a new variant of the Petya malware family. The malware combines a number of existing techniques to spread across vulnerable clients. We have begun the process of analyzing today’s samples of Petya in the lab and can report that we are able to detect and prevent infection using our SkyATP and IDP technologies. Juniper will continue to update this blog as additional information becomes available.”
By: Anushree Dixit