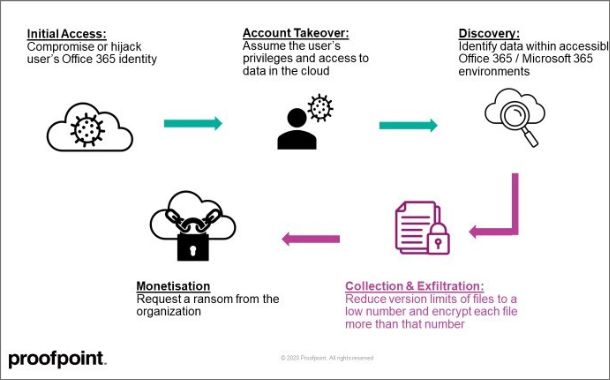
Proofpoint has discovered a potentially dangerous piece of functionality in Office 365 that allows ransomware to encrypt files stored on SharePoint and OneDrive in a way that makes them unrecoverable without dedicated backups or a decryption key from the attacker.
Once executed, the attack encrypts the files in the compromised users’ accounts. Just like with endpoint ransomware activity, those files can then only be retrieved with decryption keys. These actions can be automated using Microsoft APIs, command line interface scripts and PowerShell scripts.
OneDrive accounts are mostly used to store documents. In one example of cloud ransomware attack chain, the attacker would modify the list settings, affecting all files contained within that document library. Every document library in SharePoint Online and OneDrive has a user-configurable setting for the number of saved versions, which the site owner can change, regardless of their other roles.
There are two ways to abuse the versioning mechanism to achieve malicious aims – either by creating too many versions of a file or by reducing the version limits of a document library. Edits that increment a version of a file include changes to the document contents, filename, file metadata and the file encryption status.
Files stored in a hybrid state on both endpoint and cloud such as through cloud sync folders will reduce the impact of this novel risk as the attacker will not have access to the local/endpoint files. To perform a full ransom flow, the attacker will have to compromise the endpoint and the cloud account to access the endpoint and cloud-stored files.
Emile Abou Saleh, Regional Director, Middle East & Africa at Proofpoint, said: “With over a third of CISOs in UAE considering Cloud Account Compromise the most significant threat targeting their organizations, protecting data in the cloud is crucial. To protect against cloud account compromise, organizations should ensure they have robust security in place. Security platforms should be capable of end-to-end encryption and continuous data monitoring and detect incidents quickly to enable administrators to limit and resolve any damage.”