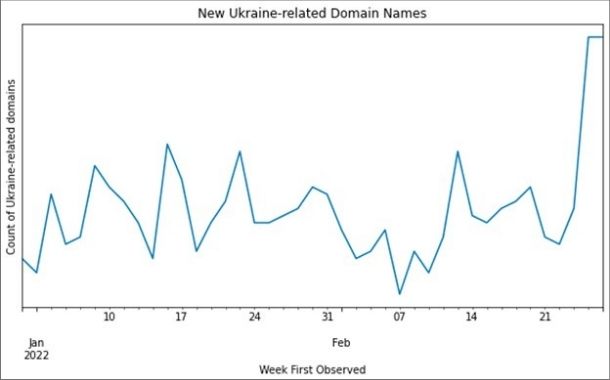
Since the Russian invasion of Ukraine on 24 February, the Infoblox Threat Intelligence Group has observed a marked increase in the number of new Ukraine-related domain names on our recursive DNS resolvers. Much of this activity is part of a global response to the humanitarian crisis happening in Eastern Europe, and some of this activity consists of new efforts led by previously uncoordinated groups.
However, cyber criminals have also seized on the opportunity and created many sites to spoof or imitate genuine support efforts. Distinguishing between these two scenarios can be difficult even for the most cautious of individuals.
Many efforts, both legitimate and fraudulent, are being established as Decentralised Anonymous Organisations
Analysis of the DNS traffic over our recursive resolvers since 24 February has shown a dramatic increase in Ukraine-related domains: from 24 to 28 February, over twice as many domains have been seen for the first time than in the week prior to the Russian offensive.
In response, Infoblox has developed multiple analytics and is actively assessing the threat level of newly observed domains. We have found indicators related to activities ranging from malware campaigns to individuals making new efforts to coordinate the delivery of medical supplies to Ukraine. Among the most prevalent threats in this environment are scams to collect cryptocurrency.
A typical DAO is focused on a specific issue, such as the war in Ukraine, and is a member-owned organisation without central leadership
One of the developments that hinders analysis is that many efforts, both legitimate and fraudulent, are being established as Decentralised Anonymous Organisations DAOs. A typical DAO is focused on a specific issue, such as the war in Ukraine, and is a member-owned organisation without central leadership.
These organisations rely on financial transaction records and rules established in a blockchain. In fact, on 26 February a Twitter account identifiable with the Ukrainian government requested cryptocurrency donations, which could have contributed to the flurry of emerging sites offering donations via virtual currency.
DAO organisations rely on financial transaction records and rules established in a blockchain
In the hours after Russian troops crossed the border with Ukraine, a number of legitimate DAOs were established to protest Russia’s actions and create financial support for Ukraine.
Perhaps most notable of these is Ukraine DAO, hosted on ukrainedao[.]love and established by Pussy Riot founder Nadya Tolokonnikova and other activists.
Due to this DAO’s new registration and use of cryptocurrency, many security vendors have falsely concluded that its hosting domain is malicious. The website for Ukraine DAO offers two methods for donating to the cause: individuals can donate cryptocurrency directly to the Ethereum wallet ukrainedao[.]eth, and individuals with an on-chain wallet can donate and receive a love token that has no monetary value but does have social impact.
In the hours after Russian troops crossed the border with Ukraine, a number of legitimate DAOs were established to protest Russia’s actions
Although hosted on a newly registered domain and utilising cryptocurrency, Ukraine DAO is publicly claimed by the founders and recognised in verified Twitter accounts. We have concluded that this domain is not hosting malware or fraudulent content.

In contrast, a number of other DAOs are more suspicious and lack credible ties to established personalities in the region. A screen capture from the domain saveukraine[.]xyz. at first glance, shows the content is similar to that of Ukraine DAO; however, based on several factors, we assess that this website is a cryptocurrency scam.
Comparing Ukraine DAO to saveukraine[.]xyz demonstrates how difficult it can be for the average consumer to distinguish between valid and nefarious activity. In addition to falsely receiving money, cyber criminals can use this interaction to steal personal information and credit cards and to deliver malware.
Cyber criminals have seized on the opportunity and created many sites to spoof genuine support efforts and distinguishing between these two can be difficult.
Opinions and comments are of the authors mentioned.