The big shift to SaaS has fragmented more than a decade’s worth of work to simplify and consolidate corporate Identity and Access Management, IAM systems. What’s more, many new SaaS applications do not integrate with organisations’ existing single sign-on, SSO solutions, yet organisations continue to accelerate adoption of new SaaS software, even without the security controls of SSO.

Adversaries will focus on finding these weaker access points, new SaaS applications to gain access to corporate and personal data, unless IT and Security departments manage to get IAM back under control.
Accelerated cloud adoption during pandemic lost sight of where sensitive data lives
Deepfakes continuing
In recent years, we have seen the increased success of blended attacks that combine social engineering tactics with malicious links, for example. With end users becoming more aware of social engineering, we can expect more sophisticated attackers will increasingly turn to deepfakes to trick end users into clicking on malicious links, downloading infected files, and the like.
Fifth generation ransomware
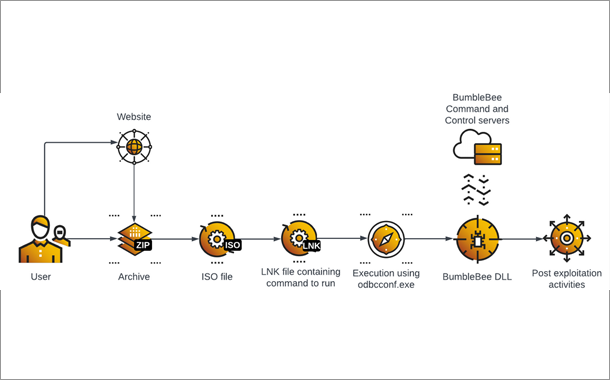
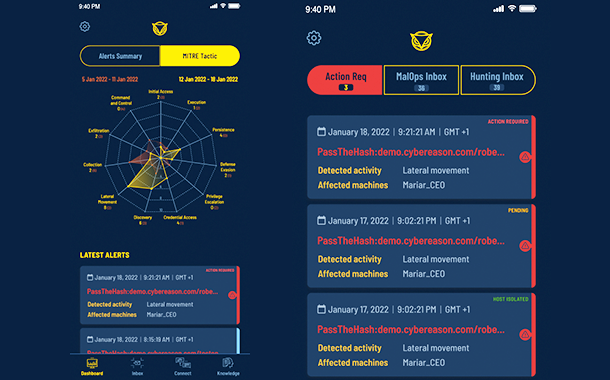
A recent report by Cybereason found that 73% of organisations suffered at least one ransomware attack in 2022, compared with just 55% in 2021. As the world reaches saturation of ransomware, adversaries will explore new methods to get money from the same victims. This will be the fifth generation of ransomware.
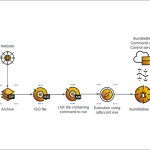
Ransomware will test cloud
Cloud storage can give organisations a significant data protection advantage, along with more flexible recovery options. But as ransomware moves from the endpoint to target cloud-only spaces, it creates new risks for organisations, especially those that accelerated cloud adoption during the pandemic and lost sight of where sensitive data lives and who has access to it. This creates weaker credential management, leaving room for ransomware to infiltrate.
Cyberattacks are transferable
The typical cyberattack moves from hacker to device, but 2023 may bring the first cyberattack that jumps between smart devices, including smart cars. We have not seen the in-smart environment replication just yet, but with the pace of innovation, a smart car attack could be riding shotgun to the vehicle next to you.
Critical national infrastructure
As both direct and indirect cyber warfare domains grow, so too does the potential for a substantial cyberattack, most likely in an area such as the energy space. This risk is most presently in EMEA, but it’s certainly top of mind among cybersecurity and national defence experts globally.
Burnout will impact cyber resilience
Security teams around the world have been working long hours from home, adapting their organisation’s security posture to support all the shifts in key business systems. In an industry that is still facing a massive skills shortage, we should not be surprised if burnout impacts security teams’ ability to maintain the round-the-clock coverage required to respond to a crisis in a timely fashion.
73% of organisations suffered at least one ransomware attack in 2022, compared with just 55% in 2021
Defenders don’t have to face an uphill fight in the battle to fend off cyberattacks. The cybersecurity industry as a whole should re-examine its threat posture and adjust its readiness footing by seeking out the right partners and implementing best practices.