The focus is on the top 10 Office 365 and Azure AD detections customers see by relative frequency. It is important to keep in mind that threat detection and response is easiest when adversaries take actions that are obviously malicious. The unfortunate reality for modern network defenders, however, is that adversaries increasingly find that such overt action is unnecessary when existing services and access used throughout an organisation can simply be co-opted, misused and abused.
This makes it critical that modern network defenders understand the intersection that may exist between the types of actions an adversary would need to take to progress towards their objectives and the behaviors routinely taken by authorised users across the enterprise. In cases where these behaviors intersect, the key factors in distinguishing the adversary and insider threat from a benign user is intent, context and authorisation.
Having the insight and knowledge that meaningful artificial intelligence can provide through constant analysation of how users access, use and configure their cloud apps, while also knowing how your hosts, accounts and workloads are being accessed— can make all the difference.
This difference can mean being able to see the clear contrast between something serious like a detection that notifies you about suspicious mail forwarding in Office 365 versus seeing a multitude of notifications that don’t pose a threat, or maybe worse—not seeing anything.
The security stakes are already at an all-time high with threats like account takeovers costing companies billions in annual losses, but the good news is that the behavior used in these criminal tactics are no longer a secret when you involve artificial intelligence.

Many of the detections represent anomalous behavior and not all of these detections are due to malicious activity. Meanwhile, some may represent infrequent behavior that is abnormal for the environment, while others may represent behavior that is against policy. Regardless of the activity, these detections still represent a large attack surface that our customers need to manage.
Without a clear expectation of what is authorised, often in the form of prescriptive policy, security defenders will have difficultly doing anything but solving for the obvious threats. That is why organisations need to have a vision for what authorised use looks like when it comes to the cloud services they adopt, which is often expressed via policy.
Vision for authorised use of cloud services should consider:
- Which services and behaviors are authorised?
- Under what context are they authorised?
- Are users authorised to leverage cloud storage and how should they interact with external entities?
- What operational parameters and safeguards are expected to accompany behaviors involving these cloud services?
Even with a clear vision, organisations quickly get into trouble when there is a lack of visibility. This is because they lack the ability to monitor and measure deviations from their vision. Solving for this challenge involves understanding the behaviors adversaries are motivated to take, and intentionally collecting and aggregating the data that uncovers these behaviors in a way that can be operationalised by security staff.
- Services: Are defenders able to detect malicious attacks carried out through enterprise cloud services? Things like detecting PowerAutomate abuse for command and control, despite the protections deployed around those capabilities?
- Management: Are defenders able to identify the misuse and abuse of administrative and management functions, such as risky exchange operations that enable adversaries and insiders to escalate privileges or to collect and exfiltrate sensitive information?
- Supply Chain: Are defenders able to uncover instances where trusted suppliers and service providers have been compromised, giving adversaries a beachhead that bypasses an organisation’s preventative and protective controls?
Security leaders should be confident answering these questions as they require more than simple compliance checks or benchmarks—these questions are best pressure tested through active investigations, threat hunts and security testing exercises.
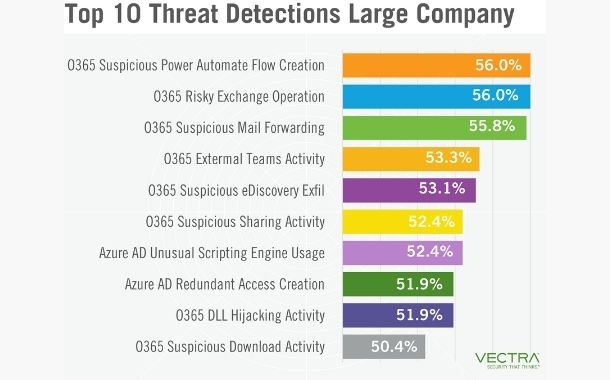
A number of these threat detections represent activities that provide ease of use, collaboration with external parties and provisioning of administrative access to the Azure AD environment. Being able to easily share documents from OneDrive or SharePoint facilitates the sharing of information with external parties, but it also provides a means for an attacker to gain access to information already in place or staged in these services.
In this instance, most of the detections are Office 365 Suspicious Download Activity, Office 365 Suspicious SharePoint Operation and Office 365 Suspicious Sharing Activity.
Some of the detections could be triggered from communicating and collaborating with external users via Microsoft Teams, which is certainly convenient for legitimate users. However, it can also be a convenient means for attackers to find useful information or obtain documents and information. It’s not uncommon to receive detections that notify about Office 365 External Teams access.
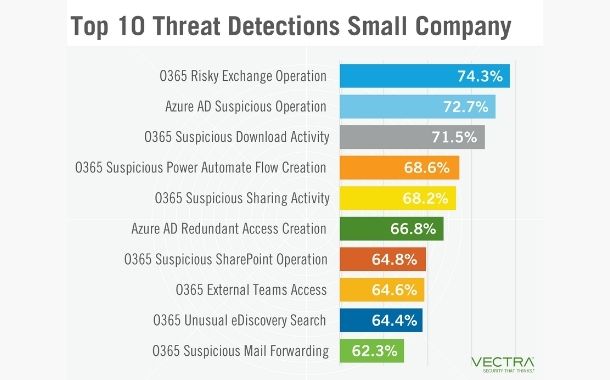
A number of these threat detections represent activities that provide ease of use, collaboration with external parties and provisioning of administrative access to the Azure AD environment.
Vectra calculated the relative frequency of threat detections that were triggered during a three-month span based on customer size. Looking at the top 10 threat detections per customer size small, medium and large—the larger the customer, the smaller the percentage of detections that trigger on a per detection type basis.
This general trend of larger companies triggering fewer detections when compared to smaller companies tells us that the larger companies’ users and administrators may perform Office 365 and Azure AD activity more consistently compared to smaller organisations.
Looking at the breakdown of which detection types were in the top 10 for each customer size, we see medium and small companies have the same top 10 threat detections, albeit with different detection type rankings. Large customers’ top 10 breakdown shows us that Office 365 DLL Hijacking, Office 365 Unusual Scripting Engine and Office 365 Suspicious eDiscovery Exfil were in the top 10, however those did not make the top 10 for medium and small companies.
Medium and small companies included Office 365 Suspicious SharePoint Operation, Office 365 Suspicious eDiscovery Search and Azure AD Suspicious Operation in their top 10, while large companies did not.
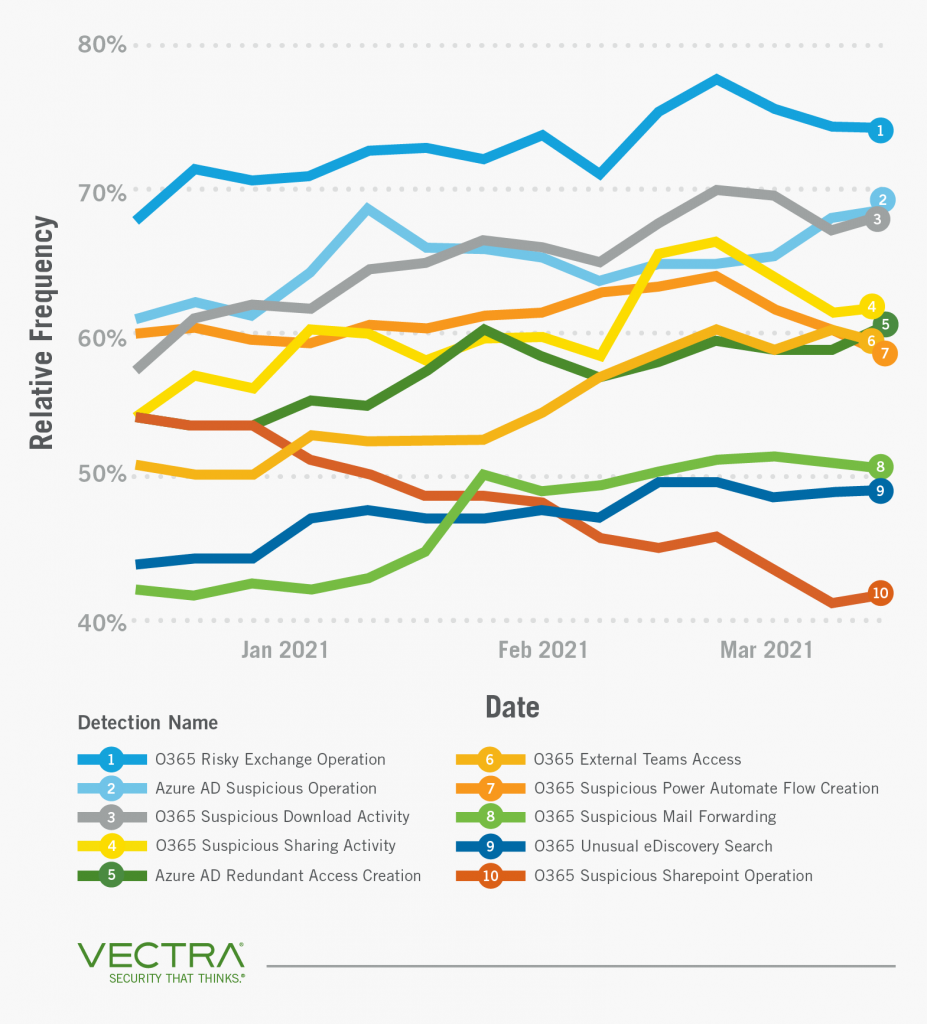
This tells us large companies have a higher prevalence of users accessing applications stored in OneDrive or SharePoint. Storage of applications in the cloud facilitates actors being able to replace or insert malicious executables and DLLs into commonly accessed shares, making the access of these file types more frequent while being less noticeable and a more effective technique for actors.
The fact that Suspicious Office 365 eDiscovery Search did not make large companies’ top 10 but Office 365 Suspicious eDiscovery Exfil did, tells us that the users who perform these types of searches at large companies generally perform eDiscovery more consistently, and pull-down data from those searches more frequently compared to smaller companies.

Office 365 eDiscovery Exfil detection will trigger on every occurrence of an account previewing or exporting data from an eDiscovery search. Access to eDiscovery provides almost complete unfettered access across all components of Office 365 to an actor, allowing them to easily search for and obtain information.
As the usage of cloud increases, end users may experience an increasing number of suspicious incidents in their usage of Azure Active Directory and Office 365.
Excerpted from the report: Vision and Visibility, Top 10 Threat Detections for Microsoft Azure AD and Office 365 by Vectra.

























