The ransomware threat, when attackers encrypt private information and hold it to ransom—became mainstream news in the 2010s following large-scale outbreaks, such as WannaCry and Cryptolocker. They targeted tens of thousands of users and often requested relatively small amounts from victims to have their files returned. Over the years, these campaigns have been on the decline.
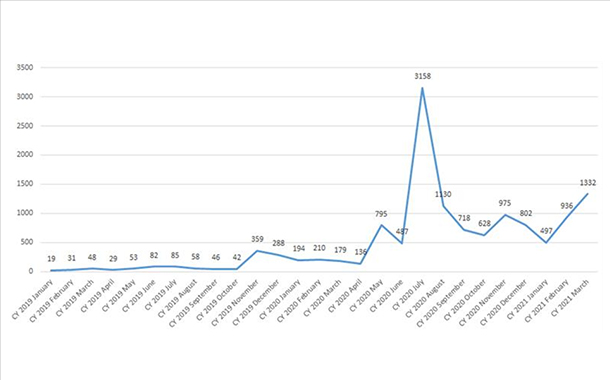
In fact, from 2019 to 2020, the total number of users that encountered ransomware across all platforms declined from 1,537,465 to 1,091,454—a decrease of 22% in the UAE. Alongside this decline, however, there has been a rise in targeted ransomware.
Targeted ransomware attacks—attacks against a chosen victim with the goal of extorting money—are often aimed at high-profile targets, such as corporations, government and municipal agencies, and healthcare organizations. The attacks involve significantly more sophistication (network compromise, reconnaissance and persistence, or lateral movement) and a much larger payout.
From 2019 to 2020, the number of users encountering targeted ransomware increased by around 767%. Some of the most prolific targeted ransomware families during this time were Maze, the infamous group involved in several loud incidents, and RagnarLocker, also covered in the news. Both of these families began the trend of exfiltration of data in addition to encrypting it and threatening to make the confidential information public if the victims refused to pay. WastedLocker also made front-page headlines with similar incidents. In many of these cases, the malware is specifically designed to infect each individual target.
Despite the rise in targeted ransomware, the ransomware family most frequently encountered by users is still WannaCry, the ransomware Trojan that first appeared in 2017 and led to damages of at least $4 billion across 150 countries. 22% of the users that encountered ransomware in 2019 encountered WannaCry; this decreased to 16% in 2020.
“The ransomware landscape has fundamentally changed since it first became big news in the security community. We’ll most likely see fewer and fewer widespread campaigns targeting everyday users. Of course, that’s not to say users aren’t still vulnerable. However, the primary focus will likely continue to be on companies and large organizations, and that means ransomware attacks will continue to become more sophisticated and more destructive. It’s imperative that businesses adopt a holistic, comprehensive set of security practices to protect their data,” comments Fedor Sinitsyn, security expert at Kaspersky.
To protect your company from ransomware, Kaspersky experts recommend that you:
- Always keep software updated on all the devices you use to prevent ransomware from exploiting vulnerabilities.
- Focus your defense strategy on detecting lateral movements and data exfiltration to the internet. Pay special attention to outgoing traffic to detect cybercriminal connections.
- Back up data regularly. Make sure you can quickly access it in an emergency when needed.
- Carry out a cybersecurity audit of your networks and remediate any weaknesses discovered in the perimeter or inside the network.
- Explain to all employees that ransomware can easily target them through a phishing email, a shady website or cracked software downloaded from unofficial sources. Ensure staff remain vigilant at all times and check their knowledge with tests.