Kaspersky researchers have revealed that the number of attacks exploiting numerous vulnerabilities in Windows Print Spooler have risen noticeably over the past four months. Even though Microsoft regularly releases patches for its Print Spooler, software that manages the printing process, cybercriminals continue to actively exploit its vulnerabilities. This gives them the opportunity to distribute and install malicious programs on victims’ computers that can steal stored data.
Over the past year, various vulnerabilities in Windows Print Spooler have been discovered. By abusing them, cybercriminals have been able to take control of servers and victims’ machines, even without a special admin access.
The most well-known vulnerabilities are CVE-2021-1675 and CVE-2021-34527 (aka PrintNightmare), which were discovered in late June 2021. PrintNightmare was accidentally published by researchers as a proof of concept exploit for a critical Windows Print Spooler vulnerability. The exploit was quickly removed from GitHub, however, some users had already managed to download it and then republished it. In late April 2022, a highly severe vulnerability (tracked as CVE-2022-22718) was also discovered in Windows Print Spooler. Microsoft had already issued a patch against this threat but the attackers were still able to exploit this vulnerability and gain access to corporate resources.
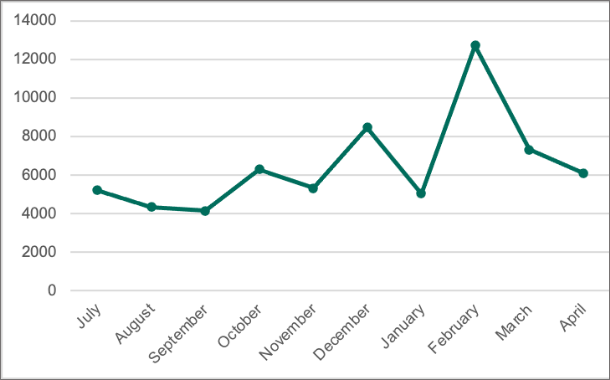
Kaspersky researchers discovered that cybercriminals made approximately 65,000 attacks between July 2021 and April 2022. Moreover, Kaspersky experts detected that roughly 31,000 of these hits occurred during the last four months, from January to April. This suggests that vulnerabilities in Windows Print Spooler remain a popular attack route for cybercriminals, which means users need to be aware of any patches and fixes that Microsoft releases.
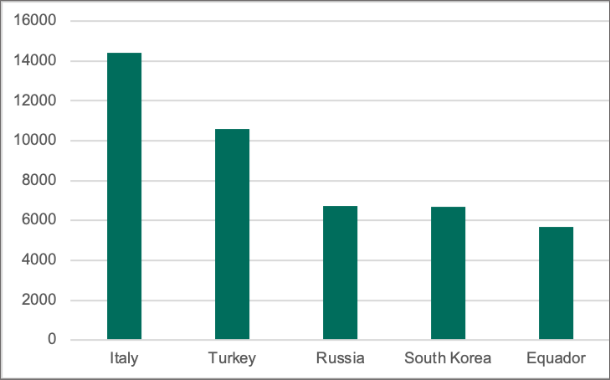
The exploitation of vulnerabilities in Windows Print Spooler has hit numerous countries, with the number of overall attacks still growing. From July 2021 to April 2022, nearly a quarter of detected hits came from Italy. After Italy, users in Turkey and South Korea were the most actively attacked. Kaspersky researchers also discovered that over the past four months attackers were most active in Austria, France and Slovenia.
“Windows Print Spooler vulnerabilities are a hotbed for emerging new threats. We anticipate a growing number of exploitation attempts to gain access to resources within corporate networks, accompanied by a high-risk of ransomware infection and data theft. Through some of these vulnerabilities, attackers can gain access not only to victims’ data but also to the whole corporate server. Therefore, it is strongly recommended that users follow Microsoft’s guidelines and apply the latest Windows security updates,” comments Alexey Kulaev, security researcher at Kaspersky.