Cybercrime is a complex landscape, but when it comes to actually launching cyberattacks, there are three main techniques that criminals have relied on for decades to help them get around organisations’ defences and into their networks: phishing, credentials theft and business email compromise. According to Verizon’s Data Breach Investigation Report, these big three are the cause 67% of all successful data breaches globally. Check Point Research recently joined forces with Otorio to analyse and take a deep dive into a large scale phishing campaign that targeted thousands of global organisations, revealing the campaign’s overall infection chain, infrastructure and how the emails were distributed.
In August, attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment. While this infection chain may sound simple, it successfully bypassed Microsoft Office 365 Advanced Threat Protection, ATP, filtering and stole over a thousand corporate employees’ credentials.
Interestingly, due to a simple mistake in their attack chain, the attackers behind the phishing campaign exposed the credentials they had stolen to the public Internet, across dozens of drop-zone servers used by the attackers. With a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attacker.

Infection chain
The initial attack started with one of several phishing email templates. The attacker would send an email imitating a Xerox or Xeros scan notification with the target’s first name or company title in the subject line.
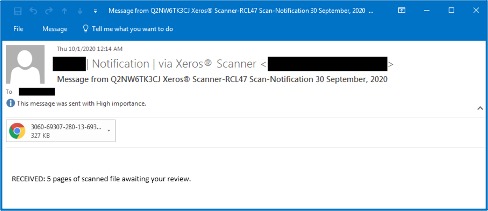
Once the victim double-clicked the attached HTML file, the default system browser displayed a blurred image with a pre-configured email within the document. Throughout the campaign several other phishing page variants were used, but the blurred background image remained the same.
After the HTML file was launched, a JavaScript code would then run in the background of the document. The code was responsible for simple password checks, sending the data to the attackers’ drop-zone server, and redirecting the user to a legitimate Office 365 login page.
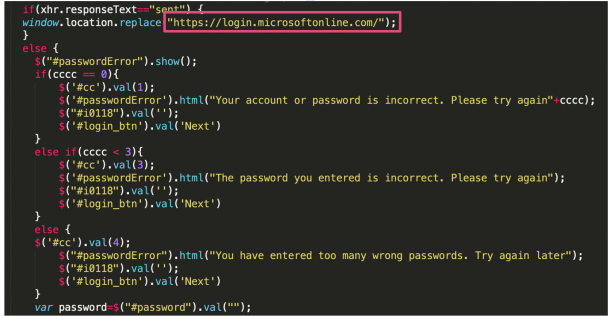
Throughout the campaign, the code was continuously polished and refined, with the attackers creating a more realistic experience so the victims were less likely to have their suspicions aroused, and more likely to provide their login credentials.
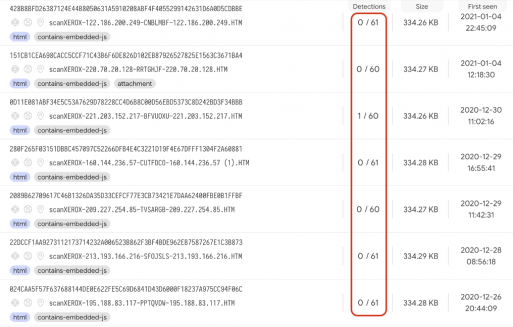
By using simple techniques, the attackers were also successful in evading detection by most Anti-Virus vendors, as can be seen from the following detection rates from the latest iteration of the campaign:
Infrastructure
This campaign utilised both unique infrastructure, and compromised WordPress websites that were used as drop-zone servers by the attackers. While using a specialised infrastructure, the server would run for roughly two months with dozens of XYZ domains. These registered domains were used in the Phishing attacks.
We discovered dozens of compromised WordPress servers that hosted the malicious PHP page named go.php, post.php, gate.php, rent.php or rest.php and processed all incoming credentials from victims of the phishing attacks.
Attackers usually prefer to use compromised servers instead of their own infrastructure because of the existing websites’ well-known reputations. The more widely recognised a reputation is, the chances are higher that the email will not be blocked by security vendors.
Email distribution
Analysing the different email headers used in this campaign allowed us to draw several conclusions regarding the Tactics Techniques & Procedures, TTPs, used by the attackers:
- The emails are sent from a Linux server hosted on Microsoft’s Azure
- The emails are often sent by using PHP Mailer 6.1.5, latest version from Mar 19 to May 27
- The emails are delivered using 1&1 email servers
Attackers used compromised email accounts to distribute spam through high-reputation phishing campaigns because the emails are harder to block. In one specific campaign, we found a phishing page impersonating IONOS by 1&1, a German web hosting company. It is highly likely that the compromised IONOS account credentials were used by the attackers to send the rest of the Office 365 themed spam.
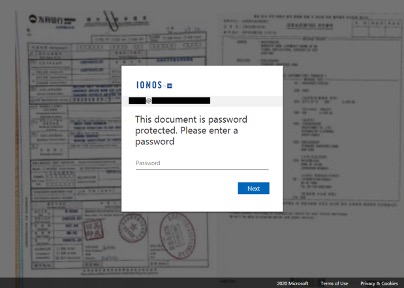
Targeted organisations
We found that once the users’ information was sent to the drop-zone servers, the data was saved in a publicly visible file that was indexable by Google. This allowed anyone access to the stolen email address credentials with a simple Google search. The public availability of this data allowed us to create a breakdown of the victims according to their industry, based on a subset of approx. 500 stolen credentials
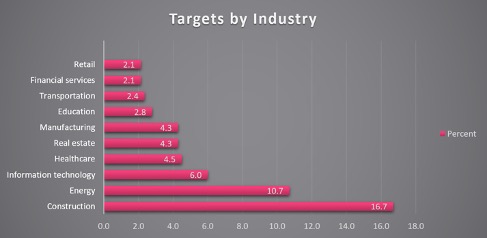
Although there was a wide distribution of targeted industries, there appears to be a special interest in Energy and Construction companies.
Lotem Finkelsteen, Head of Threat Intelligence, Check Point Software said, “We tend to believe that when someone steals our passwords, the worst case scenario is that the information will be used by hackers who exchange them through the dark net. Not in this case. Here, the entire public had access to the information stolen. The strategy of the attackers was to store stolen information on a specific webpage that they created. That way, after the phishing campaigns ran for a certain time, the attackers can scan the compromised servers for the respective webpages, collecting credentials to steal. The attackers didn’t think that if they are able to scan the internet for those pages, Google can too. This was a clear operation security failure for the attackers.”

























