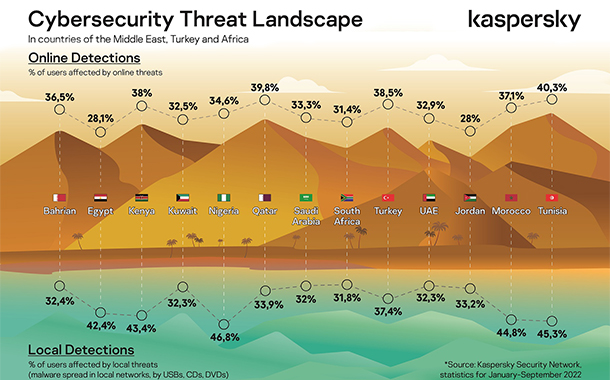
2022 was marked by a 20th century-style military conflict – that definitely brought uncertainty and some serious risks. A number of cyber-events took place during the conflict turned to be very significant.

Significant signs and spikes in cyberwarfare in the days and weeks pre-dating military conflict were seen. February 24, 2022 saw a massive wave of pseudo-ransomware and wiper attacks indiscriminately affecting Ukrainian entities. Some were highly sophisticated, but the volume of wiper and ransomware attacks quickly subsided after the initial wave, with a limited number of notable incidents subsequently reported. Ideologically-motivated groups that presented themselves in the original wave of attacks appear to be inactive now.
On February 24, Europeans relying on the ViaSat-owned satellite faced major internet access disruptions. This cyber-event started around 4h UTC, less than two hours after the Russian Federation publicly announced the beginning of a special military operation in Ukraine. The ViaSat sabotage once again demonstrates cyberattacks are a basic building block for modern armed conflicts and may directly support key milestones in military operations.
There is no evidence that cyberattacks were part of coordinated military actions on either side
As the conflict has evolved, there is no evidence that the cyberattacks were part of coordinated military actions on either side. However, there are some main characteristics that defined the 2022 cyber confrontation:
Hacktivists and DDoS attacks
The conflict in Ukraine has created a breeding ground for new cyberwarfare activity from various groups including cybercriminals and hacktivists, rushing to support their favourite side. Some groups such as the IT Army of Ukraine or Killnet have been officially supported by governments and their Telegram channels include hundreds of thousands of subscribers.
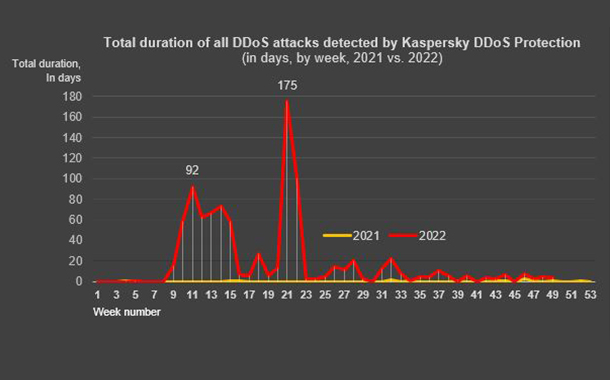
While the attacks performed by hacktivists had relatively low complexity, the experts witnessed a spike in DDoS activity during summer period – both in number of attacks and their duration: in 2022, an average DDoS attack lasted 18.5 hours – almost 40 times longer compared to 2021, approx. 28 minutes.
Hack and leak
The more sophisticated attacks attempted to hijack media attention with hack-and-leak operations, and have been on the rise since the beginning of the conflict. Such attacks involve breaching an organisation and publishing its internal data online, often via a dedicated website. This is significantly more difficult than a simple defacing operation, since not all machines contain internal data worth releasing.
Weaponizing open-source software
As the conflict drags on, popular open-source packages can be used as a protest or attack platform by developers or hackers alike. The impact from such attacks can extend wider than the open-source software itself, propagating in other packages that automatically rely on the trojanised code.
Balkanisation
Following the start of the Ukraine conflict in February 2022, many western companies are exiting the Russian market and leaving their users in a delicate position when it comes to receiving security updates or support – and the security updates are probably the top issue when vendors end support for products or leave the market.
As the metaverse experience is universal and does not obey regional data protection laws, this might create complex conflicts
From February 24 onwards, we have been puzzled with a question, if cyberspace is a true reflection of the conflict in Ukraine, it represents the pinnacle of a real, modern cyberwar. By going through all the events that followed military operations in cyberspace, we witnessed an absence of coordination between cyber and kinetic means, and in many ways downgraded cyber-offense to a subordinate role.
Metaverse
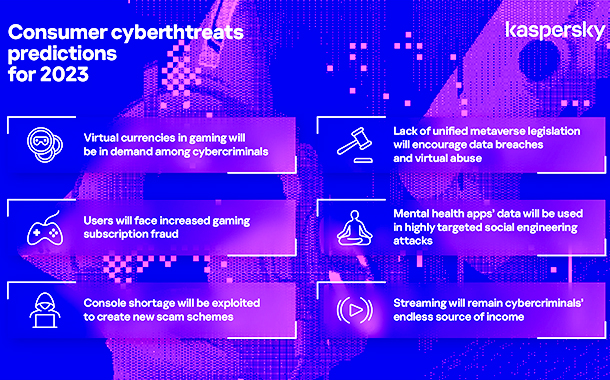
New social media will bring more privacy risks. We would like to believe that the near future will see a new revolutionary phenomenon in the world of social networks. Perhaps this will happen already in VR, but rather in AR. As soon as a new trendy app appears, so do risks for its users. Privacy most probably will be a major concern, too, as many start-ups neglect to configure their applications in accordance with privacy protection best practices. This attitude may lead to a high risk of personal data compromise and cyberbullying in the new social media, however trendy and convenient it may be.
Right now, we are only taking the first steps toward complete immersion in virtual reality, already using metaverses for entertainment while testing industrial and business applications of this new technology. Although so far, there are only a few metaverse platforms, they already have revealed risks that future users will face. As the metaverse experience is universal and does not obey regional data protection laws, such as GDPR, this might create complex conflicts between the requirements of the regulations regarding data breach notification.
Virtual abuse and sexual assault will spill over into metaverses. We have already seen cases of avatar rape and abuse, despite efforts to build a protection mechanism into metaverses. As there are no specific regulation or moderation rules, this scary trend is likely to follow us into 2023.
Personal data
As usage of mental health apps increases, the risk of this sensitive data being accidentally leaked or obtained by a third party through a hacked account will also grow. Armed with details on the victim’s mental state, the attacker is likely to launch an extremely precise social engineering attack. Now, imagine that the target is a key employee of a company.
We are likely to see stories of targeted attacks involving data on the mental health of corporate executives. And, if you add here data, such as facial expressions and eye movement, that sensors in VR headsets collect, the leakage of that data may prove disastrous.