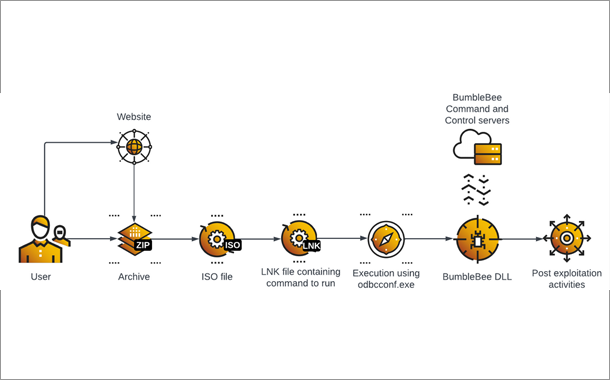
When it comes to ransomware, what we see today is not that simple. We now have ransomware cartels, like REvil, Conti, DarkSide, and others, and ransomware is not a piece of malware, but rather comprehensive ransomware operations, or RansomOps, where the execution of the ransomware itself is just the final piece of a much longer attack chain.
There is too much focus on the ransomware executable, or how to recover once an organisation’s servers and data are already encrypted. That’s like fighting terrorism by focusing only on the explosive device or waiting to hear the boom to know where to focus resources.
Rather than attacking 100 or 1,000 separate organisations, they can successfully exploit one company
RansomOps take a low and slow approach, infiltrating the network and spending time moving laterally and conducting reconnaissance to identify and exfiltrate valuable data. Threat actors might be in the network for days, or even weeks.
It’s important to understand how RansomOps work and be able to recognise Indicators of Behaviour that enable you to detect and stop the threat actor before the point of detonation when the data is actually encrypted, and a ransom demand is made.
RansomOps take a low and slow approach, infiltrating the network and spending time moving laterally
There is a growing trend of threat actors realising the value of targeting a supplier or provider up the chain in order to compromise exponentially more targets downstream. Rather than attacking 100 or 1,000 separate organisations, they can successfully exploit one company that unlocks the door to all the rest. It is the path of least resistance.
The attacks we have seen have been part of cyber espionage campaigns from nation-state adversaries. Those attacks will likely continue, and we will see a rise in cybercriminals adopting the strategy as well. Companies that act as suppliers or providers need to be more vigilant, and all organisations need to be aware of the potential risk posed from the companies they trust.
Microsoft has a dominant role across operating systems, cloud platforms, applications that makes it fairly ubiquitous
The simple truth is that one way or another, Microsoft products are directly involved in the vast majority of cyber-attacks. Threat actors invest their time and effort identifying vulnerabilities and developing exploits for the platforms and applications their potential victims are using. Microsoft has a dominant role across operating systems, cloud platforms, and applications that make it fairly ubiquitous.
As such, Microsoft will continue to be the primary focus for cyber-attacks in 2022. That is not really a revelation. Defenders need to understand the risk of relying on Microsoft to protect them when they cannot even protect themselves. Organisations that depend on Microsoft for security will find themselves making headlines for the wrong reasons.
I am not suggesting that organisations not use Microsoft products or services, but it is important to understand the risks and have a layered approach to defending those products and services against attacks.
What we need to be aware of as we go into 2022 is the increasing cooperation and collaboration between threat actors
The line no longer exists between national security and cybersecurity. Sometimes a nation-state adversary attacks a private company as part of a broader campaign and sometimes cybercriminals launch attacks with national security implications.
What we need to be aware of as we go into 2022 is the increasing cooperation and collaboration between these threat actors. Nation-state adversaries are not directly controlling many of these operations, but a combination of state-sanctioned, state-condoned, and state-ignored attacks create an environment where failure to act is equivalent to tacit approval and indicates that even if they are not actively working together, their objectives are often aligned.
Microsoft will continue to be the primary focus for cyberattacks in 2022 and defenders need to understand the risk of relying on Microsoft to protect them.